Microsoft Services for NFS
129
NAS 1500s and 500s Administration Guide
Squashed mappings
If the NFS server does not have a corresponding UID or GID or if the administrator has set
other conditions to filter out the user, a process called squashing takes effect. Squashing is the
conversion of an unmapped or filtered user to an anonymous user. This anonymous user has
very restricted permissions on the system. Squashing helps administrators manage access to
their exports by allowing them to restrict access to certain individuals or groups and to squash
all others down to restricted (or no) access. Squashing enables the administrator to allow
permissions instead of denying access to all the individuals who are not supposed to have
access.
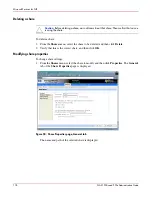
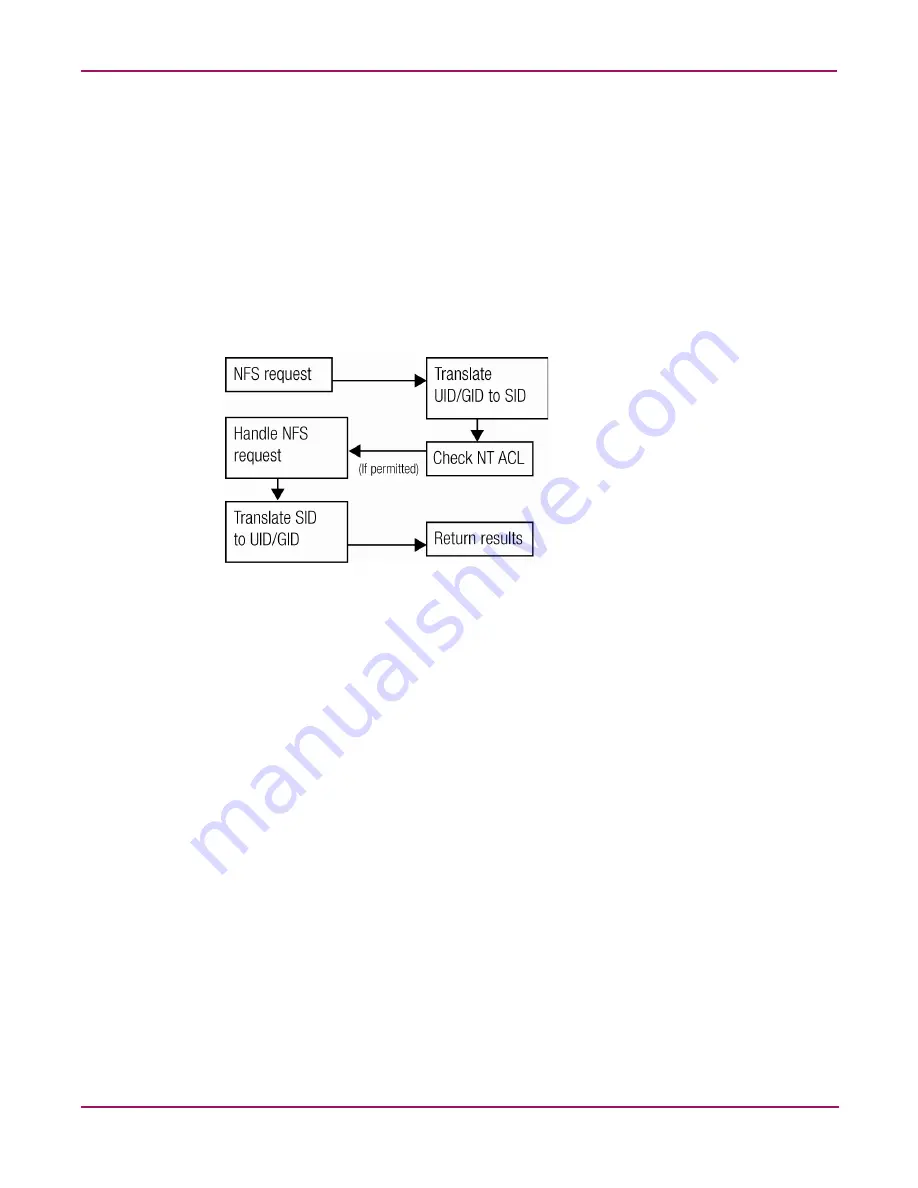
Figure 66
is a diagram showing an example of how the mapping server works for an ls -al
command.
Figure 66: Mapping Server “ls -al” Command example
A double translation, as illustrated in
Figure 66
, is sometimes necessary because some
commands return user ID information. For example, if the NFS request issued was an
ls -al
command, the return listing of files contains user information (the user and group that own the
file). The
ls -al
command is a UNIX command. It returns a long or full listing of all files.
Because this information is contained in a Windows NT Access Control List (ACL), it is not
UNIX ready. The ACL information has to be converted back to UNIX UIDs and GIDs for the
UNIX systems to understand and display the user information.
This second translation is not done for commands that do not return user information. For
example, if the NFS request were just to read data from or write data to a file, the second
translation would not be performed because there is no returning user information.
User name mapping best practices
Below is a brief list of suggested practices:
■
Back up user and group mappings
To avoid loss of complex advanced mappings in the case of a system failure, back up the
mappings whenever the mappings have been edited or new mappings have been added.
■
Map consistently
Groups that are mapped to each other should contain the same users and the members of
the groups should be properly mapped to each other to ensure proper file access.
Example using User1 and Group1:
— Make sure that the Windows User1 is mapped to the corresponding UNIX User1.