200
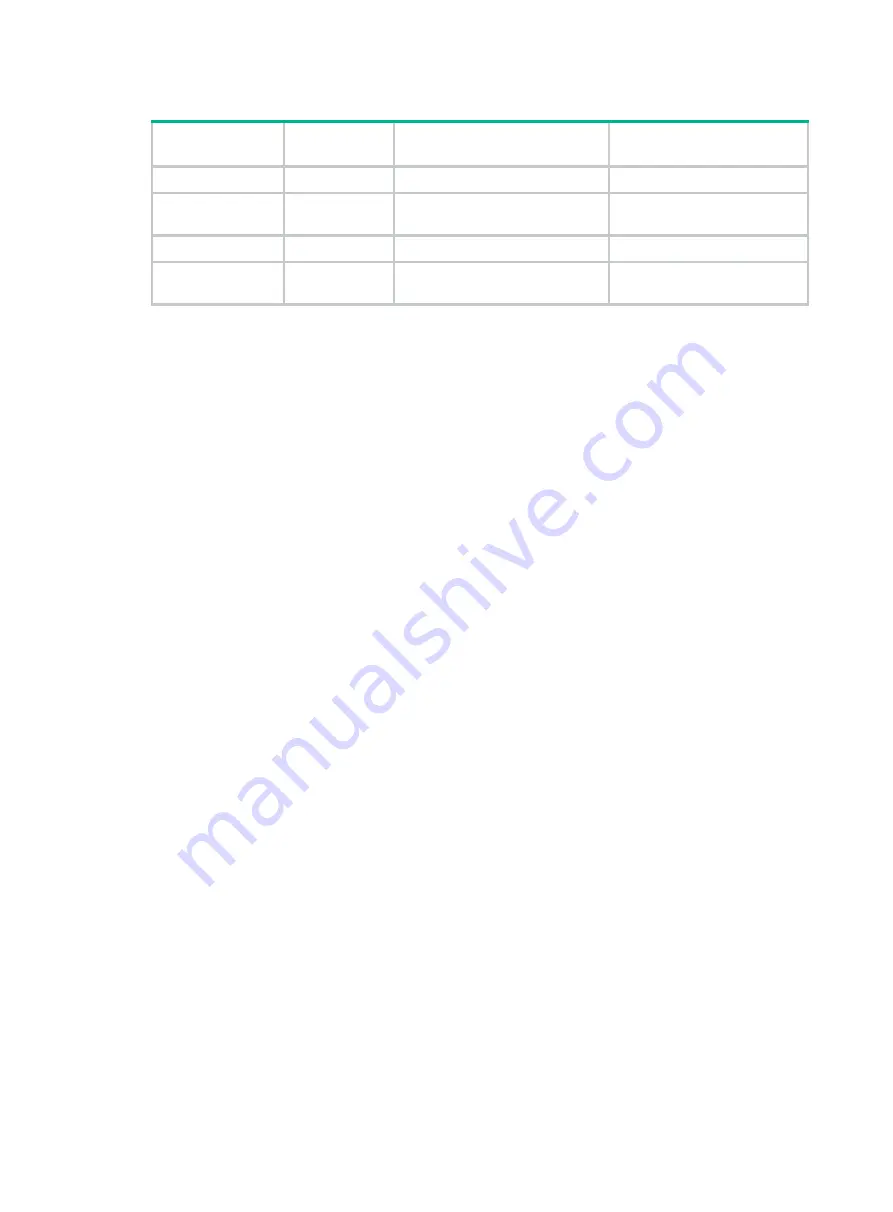
Table 45 Encrypted privacy key length requirements
Authentication
algorithm
Encryption
algorithm
Hexadecimal string
Non-hexadecimal string
MD5
3DES
64 characters
73 characters
MD5
AES128 or
DES-56
32 characters
53 characters
SHA
3DES
80 characters
73 characters
SHA
AES128 or
DES-56
40 characters
53 characters
acl
acl-number
: Specifies a basic IPv4 ACL to filter NMSs by source IPv4 address. The
acl-number
argument represents an ACL number in the range of 2000 to 2999. Only NMSs with an IPv4 address
permitted in the ACL can use the specified username to access the SNMP agent. If no ACL is
specified, or the specified ACL does not exist, any NMS can use the specified username to access
the SNMP agent. If the specified ACL does not have any rules, no NMS in the SNMP community can
access the SNMP agent.
acl
ipv6
ipv6-acl-number
: Specifies a basic IPv6 ACL to filter NMSs by source IPv6 address. The
ipv6-acl-number
argument represents an ACL number in the range of 2000 to 2999. Only NMSs with
an IPv6 address permitted in the IPv6 ACL can use the specified username to access the SNMP
agent. If no ACL is specified, or the specified ACL does not exist, any NMS can use the specified
username to access the SNMP agent. If the specified ACL does not have any rules, no NMS in the
SNMP community can access the SNMP agent.
local
: Specifies the local SNMP engine.
engineid
engineid-string
: Specifies an SNMP engine. The
engineid-string
argument represents the
engine ID and must contain an even number of hexadecimal characters, in the range of 10 to 64.
All-zero and all-F strings are invalid. After you change the local engine ID, the existing SNMPv3
users and encrypted keys become invalid, and you must reconfigure them.
Usage guidelines
SNMPv3 users are valid only on the SNMP engine that creates them. By default, SNMPv3 users are
created on the local SNMP engine. When you create an SNMPv3 user for sending SNMP inform
messages, you must associate it with the remote SNMP engine.
To send SNMPv3 informs to an NMS, perform the following tasks:
•
Specify the IPv4 or IPv6 address of the NMS in the
snmp-agent
usm-user
v3
command.
•
Map the IPv4 or IPv6 address to the SNMP engine ID of the NMS by using the
snmp-agent
remote
command.
You can use the following modes to control access to MIB objects for an SNMPv3 user:
•
View-based
Access
Control
Model
—In VACM mode, you must create an SNMPv3 group
before you assign an SNMPv3 user to the group. Otherwise, the user cannot take effect after it
is created. An SNMP group contains one or multiple users and specifies the MIB views and
security model for the group of users. The authentication and encryption algorithms for each
user are specified when they are created.
•
Role based access control
—The RBAC mode controls access to MIB objects by assigning
user roles to SNMP users.
{
An SNMP user with a predefined user role network-admin, mdc-admin, or level-15 has the
read and write access to all MIB objects.
{
An SNMP user with a predefined user role network-operator or mdc-operator has the
read-only access to all MIB objects.
{
An SNMP user with a user role specified by the
role
command accesses MIB objects
through the user role rules specified by the
rule
command.
















































