LTE CPE B2368 User's
Guide
5 Wireless WiFi 2.4 / 5 GHz
Issue 01
Copyright © Huawei Technologies Co., Ltd.
45
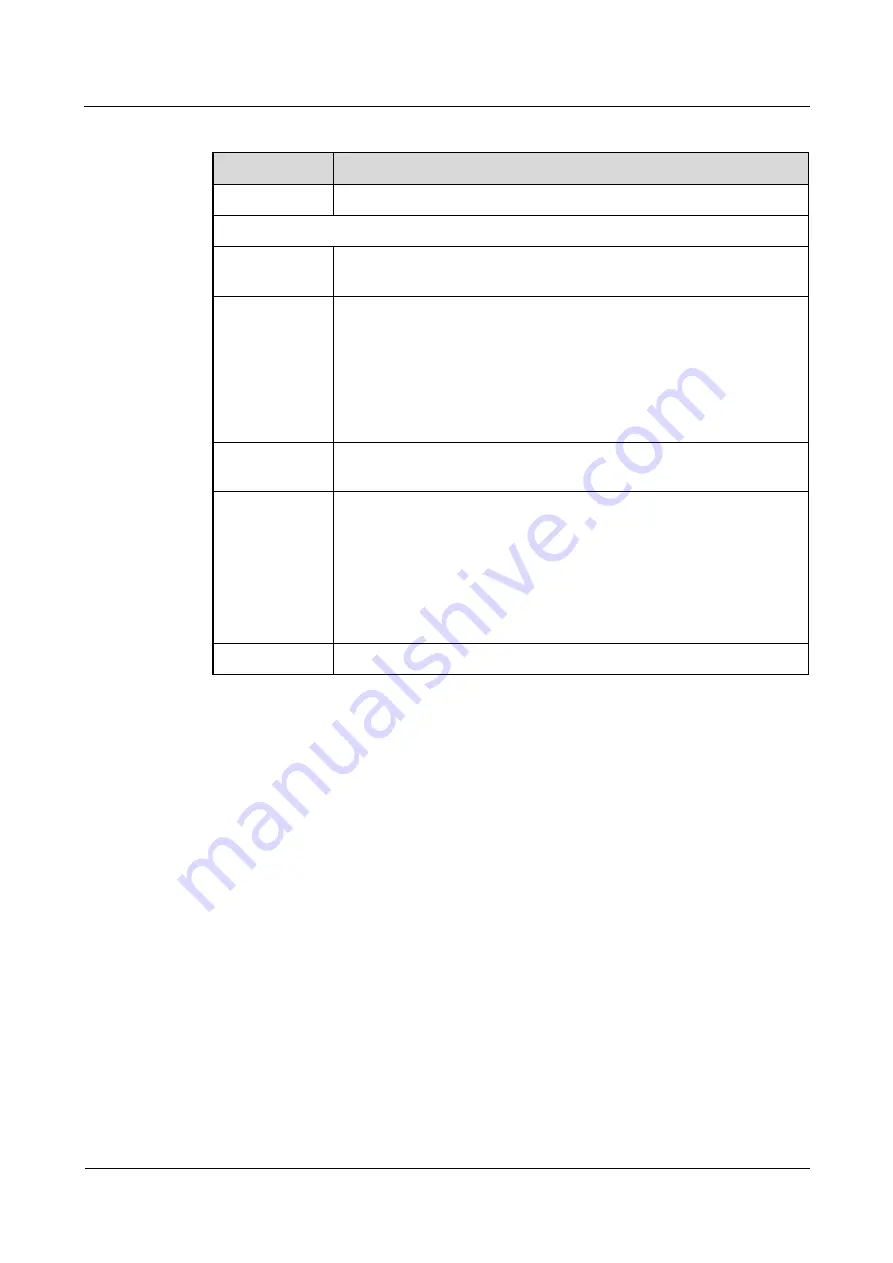
Table 5-6
Network Settings> WiFi 2.4 GHz / 5 GHz WiFi> WPS
Table 5-6
Network Settings> WiFi 2.4 GHz / 5 GHz WiFi> WPS
Item
Description
WPS
selecting
Allow
LTE modem to turn on the WPS.
selecting
Allow
LTE modem to turn on the WPS.
selecting
Allow
LTE modem to turn on the WPS.
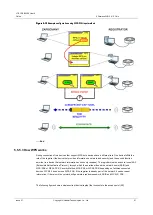
Add new device using WPS
PBC Method 1 Use this method to set up a wireless network via the
WPS pressing.
WPS
Click this button to add a new wireless network devices that support WPS (which is
within range of an LTE modem). WPS button on the client device may be a physical
button on the outside of the device, or as a software button, like button
WPS
on this screen.
WPS
on this screen.
Note: WPS button on the wireless device is required to press two minutes from clicking
on this button.
Method 2 PIN
Use this method to set up a wireless network by entering PIN client device.
Register
Enter the PIN of the client device you want to connect via WPS, and then click
Register
Enter the PIN of the client device you want to connect via WPS, and then click
Register
to connect to a wireless network.
The PIN code can be located on the outside of the device or its configuration
interface.
Note: The WPS on the client device also must be activated within two minutes of
entering a PIN.
Use
Clicking
Use
save your changes.
Clicking
Use
save your changes.
Clicking
Use
save your changes.
5.5 Technical details
This chapter deals with the technical details of the wireless LAN.
5.5.1 Overview of wireless security
All radio communication is by its nature very easy to catch. For wireless data networks, this means that anyone who is
within range of a wireless network without security can not read data that pass through the air waves, but also connect to
the network. Once an unauthorized person gets access to the network once, can not gain access to sensitive information,
but also to expand the network of malicious software with the intent network and the connected equipment damage. For
this reason, many developed safety systems designed to ensure that the use of wireless networks and understanding of
data flowing on the network has been designed exclusively to authorized persons.
These safety standards do two things. First used for access authentication. This means that access to the network will
receive only the person or device that know the correct credentials (username and password, respectively. Key).
Second, encrypted wireless communication. This means that the information sent by air are in a readable format - They
Second, encrypted wireless communication. This means that the information sent by air are in a readable format - They
Second, encrypted wireless communication. This means that the information sent by air are in a readable format - They
are encoded. Only a person possessing the relevant key data they are able to read, and this key will get only persons
authenticated credentials.