Version 2.1 (May 2016)
48
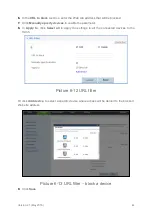
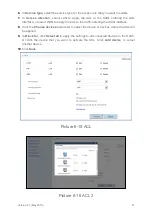
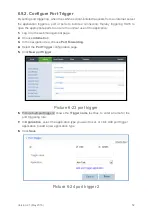
6.7. Configure DMZ
After DMZ is enabled, the computer that is configured as a DMZ host is exposed to the
Internet. For example, when building a server, you can configure the computer providing
external services as a DMZ host, which helps protect other computers on the home
network.
1.
Log in to the web management page.
2.
Choose
Internet
tab.
3.
In the navigation tree, choose
Network Security
.
4.
Select the
DMZ
configuration page.
5.
In
Host address
, select the device that you want to act as a DMZ host, or click
Add
device
to add a new DMZ host.
6.
Set
Enable DMZ
to enable the capability.
7.
Click
Save
.
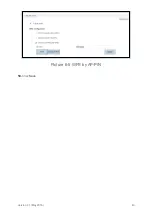
Picture 6-17 DMZ
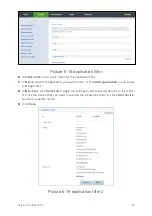
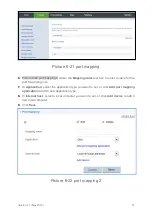
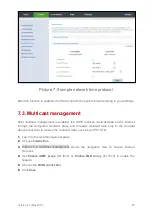
6.8. Configure Application Filter
To enable the application filter function on a specified computer, you can block network
attacks from applications to the specified computer.
1.
Log in to the web management page.
2.
Choose
Internet
tab.
3.
In the navigation tree, choose
Network Security
.
4.
Select the
Application Filter
configuration page.
5.
Click
New application filter
.