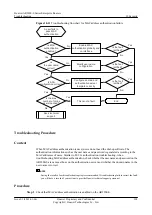
Step 4
Run the
display arp anti-attack gateway-duplicate item
command to check the anti-collision
entries.
l
If an entry is displayed, you can view it to find the IP address, MAC address, and source
interface of the attacker. Add the attacker to the blacklist or configure a blackhole MAC entry
according to attacker information. Subsequently, packets from the attacker will be discarded.
l
If no entry is displayed, go to step 5.
Step 5
Collect the following information and contact Huawei technical support personnel:
l
Results of the preceding troubleshooting procedure
l
Configuration file, log file, and alarm file of the AR2200-S
----End
Relevant Alarms and Logs
Relevant Alarms
l
1.3.6.1.4.1.2011.5.25.165.2.2.2.1
Relevant Logs
None.
10.2.3 User Traffic Is Interrupted by a Large Number of Bogus ARP
Packets
Common Causes
This fault is commonly caused by the following:
l
An attacker sends a large number of bogus ARP packets , thus increasing the load of the
destination network segment. These ARP packets are sent to the CPU, causing a high CPU
usage. DoS attacks may also be initiated in this case.
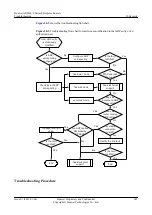
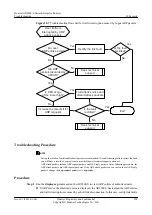
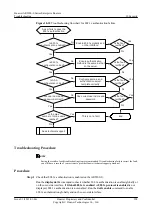
Troubleshooting Flowchart
The AR2200-S uses the CPCAR mechanism to limit the rate of ARP packets sent to the CPU.
If an attacker sends a large number of bogus ARP packets, valid ARP packets are also discarded
when the bandwidth limit is exceeded. Consequently, user traffic is interrupted.
shows the troubleshooting flowchart.
Huawei AR2200-S Series Enterprise Routers
Troubleshooting
10 Security
Issue 01 (2012-01-06)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
289