To initiate a SYN Flood attack, an attacker sends a SYN packet with a forged or nonexistent
source address to connect to a server. After receiving the SYN packet, the server replies with a
SYN-ACK packet. The receiver of the SYN-ACK packet does not exist, so a half-connection is
generated. If the attacker sends a large number of these packets, many half-connections are
generated on the attacked host. The resources on the attacked host are exhausted and users cannot
access the host until the half-connections time out.
Common Causes
This fault is commonly caused by one of the following:
l
SYN Flood attack defense is not enabled.
l
The packet rate threshold on the firewall is set to a large value.
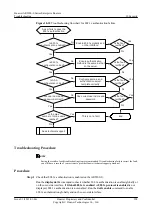
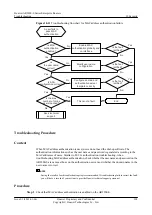
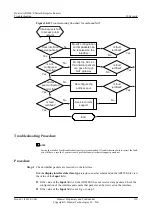
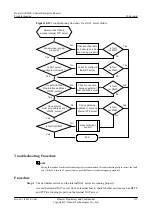
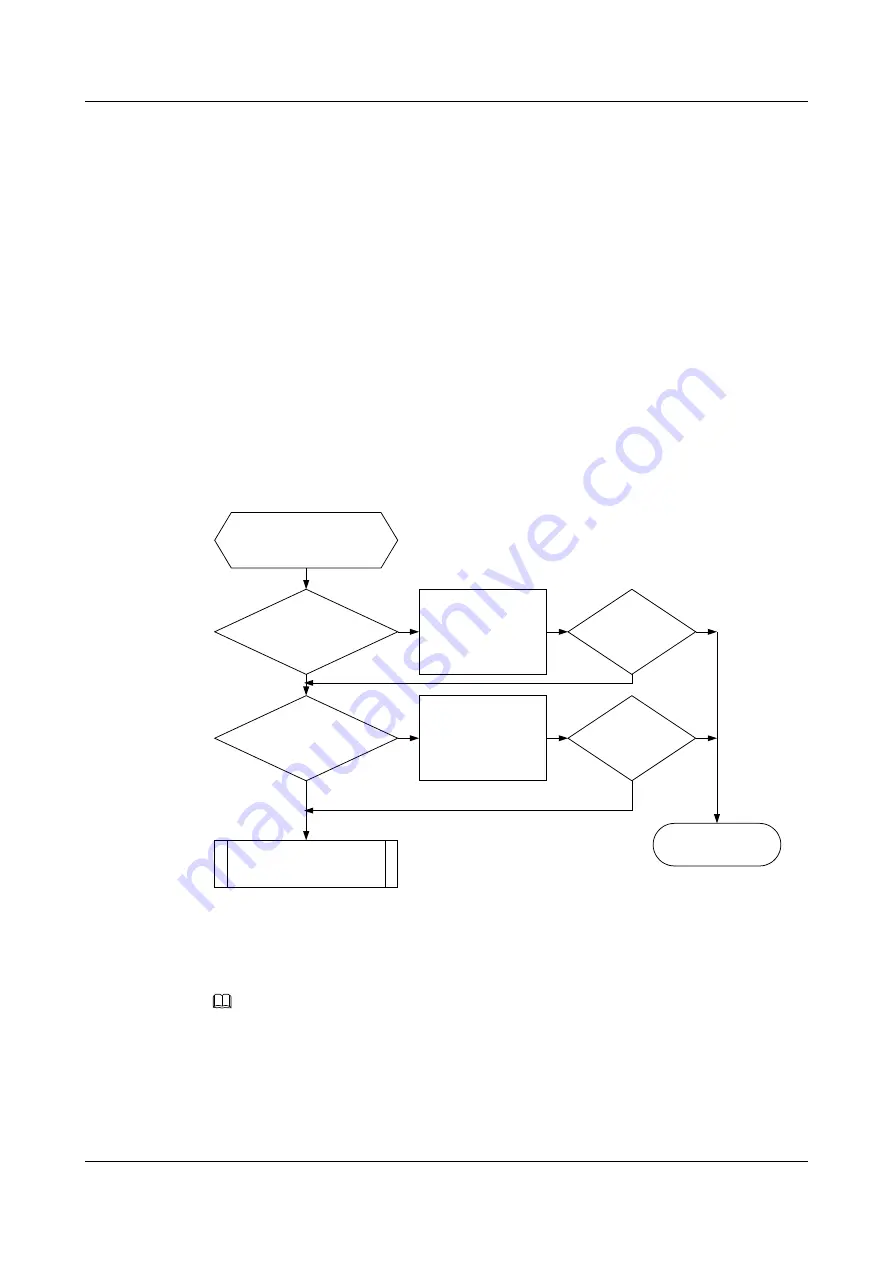
Troubleshooting Flowchart
shows the troubleshooting flowchart for SYN Flood attack defense.
Figure 10-12
Troubleshooting flowchart for SYN flood attack defense
SYN-Flood attack
defense is invalid
Is attack
defense enabled?
Enable SYN-
Flood attack
defense
Is the fault
rectified?
Is packet rate
threshold too large?
Reconfigure
packet rate
threshold
Is the fault
rectified?
Seek technical
support
End
No
No
No
No
Yes
Yes
Yes
Yes
Troubleshooting Procedure
NOTE
Saving the results of each troubleshooting step is recommended. If troubleshooting fails to correct the fault,
you will have a record of your actions to provide Huawei technical support personnel.
Procedure
Step 1
Check that SYN Flood attack defense is enabled.
Huawei AR2200-S Series Enterprise Routers
Troubleshooting
10 Security
Issue 01 (2012-01-06)
Huawei Proprietary and Confidential
Copyright © Huawei Technologies Co., Ltd.
306