| Installation and Upgrades |
17
Changing and Securing the TCP Port
SSH servers, including the OpenSSH suite included with your product, listen for incoming connections on TCP Port
22 by default. As such, Port 22 is subject to numerous unauthorized login attempts by hackers who attempt to access
unsecured servers. An effective deterrent is to close Port 22 and run the service on a seemingly random port above
1024 (and up to 65535).
To standardize the port for use in Aspera transfers, Aspera recommends setting the TCP port to 33001 and closing
TCP/22.
Prerequisites:
• Before changing the default port for SSH connections, verify with your network administrators that TCP/33001 is
open.
• Before closing port TCP/22, notify users of the change.
Notifying Users - How to Specify TCP/33001
Aspera recognizes that disabling the default SSH connection port (TCP/22) might affect your clients. When you
change the port, ensure that you advise your users on how to configure the new port number, from the GUI (if
available and used) and from the command line.
•
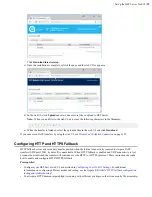
GUI:
To change the SSH port in Desktop Client, click
Connections
and select the entry for the server whose ports
are changing. On the
Connection
tab, click
Show Advanced Settings
and enter the SSH port number in the
SSH
Port (TCP)
field.
•
Command line:
Clients running FASP transfers from the command line can specify the port by using the
-P
33001
option.
Changing to TCP/33001
The following steps require root privileges.
1.
Open the SSH configuration file.
/etc/ssh/sshd_config
2.
Add the TCP/33001 SSH port and close TCP/22.
Comment out the line for "Port 22" and add a line for "Port 33001":
#Port 22
Port 33001
Note:
If you are using the HST Server web UI, you must also update the
SshPort
value in the
<WEB...>
section of
aspera.conf
. For details, see
Configuring your Web UI Settings
on page 25.
Once this setting takes effect:
• Aspera clients must set the transfer port to 33001 in the GUI or specify
-P 33001
for command line
transfers.
• Server administrators should use
ssh -p 33001
to access the server through SSH.
3.
Disable non-admin SSH tunneling.
These instructions require that OpenSSH 4.4 or newer is installed on your system in order to use the
Match
directive.
Match
allows you to selectively override certain configuration options when specific criteria (based on
user, group, hostname, or address) are met.
Open your SSH Server configuration file,
sshd_config
, with a text editor. Add the following lines to the end
of the file (or modify them if they already exist):
AllowTcpForwarding no
Match Group root
AllowTcpForwarding yes