| Watch Folders and the Aspera Watch Service |
187
Field
Description
Default
•
HIGH
•
LOW
min_rate
Attempt to transfer no slower than the specified minimum transfer
rate.
0B
target_rate
The target transfer rate. Transfer at rates up to the specified target
rate. This option accepts suffixes T for terabits/s, G for gigabits/
s, M for megabits/s, K for kilobits/s, or B for bits/s. Decimals are
allowed. If this option is not set by the client, the setting in the
server's
aspera.conf
is used. If a rate cap is set in the local or
server
aspera.conf
, the rate does not exceed the cap.
10M
tcp_port
The port to use for SSH connections.
22
udp_port
The port to use for UDP connections.
33001
read_blk_size
The read block size.
Default determined
by settings in
aspera.conf
write_blk_size
The write block size.
Default determined
by settings in
aspera.conf
datagram_size
The datagram size (MTU) for FASP.
Uses the detected
path MTU.
rexmsg_size
The maximum size of a retransmission request. Maximum: 1440.
Determined by
ascp
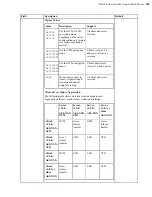
cipher
The encryption cipher that is used to encrypt data in transit. Aspera
supports three sizes of AES cipher keys (128, 192, and 256 bits) and
supports two encryption modes, cipher feedback mode (CFB) and
Galois/counter mode (GCM). The GCM mode encrypts data faster
and increases transfer speeds compared to the CFB mode, but the
server must support and permit it.
Cipher rules
The encryption cipher that you are allowed to use depends on the
server configuration and the version of the client and server:
• When you request a cipher key that is shorter than the cipher
key that is configured on the server, the transfer is automatically
upgraded to the server configuration. For example, when the
server setting is AES-192 and you request AES-128, the server
enforces AES-192.
• When the server requires GCM, you must use GCM (requires
version 3.9.0 or newer) or the transfer fails.
• When you request GCM and the server is older than 3.8.1 or
explicity requires CFB, the transfer fails.
• When the server setting is "any", you can use any encryption
cipher. The only exception is when the server is 3.8.1 or older
and does not support GCM mode; in this case, you cannot
request GCM mode encryption.
• When the server setting is "none", you must use "none". Transfer
requests that specify an encryption cipher are refused by the
server.
AES128