| Appendix |
341
a) Retrieve the server's SHA-1 fingerprint.
# cat /etc/ssh/ssh_host_rsa_key.pub | awk '{print $2}' | base64 - |
sha1sum
b) Set the SSH host key fingerprint in
aspera.conf
.
# asconfigurator -x
"set_server_data;ssh_host_key_fingerprint,
fingerprint
"
This command creates a line similar to the following example of the
<server>
section of
aspera.conf
:
<ssh_host_key_fingerprint>7qdOwebGG2dP3HmWfP3
</ssh_host_key_fingerprint>
c) Restart the node service to activate your changes.
Run the following commands to restart
asperanoded
:
# systemctl restart asperanoded
or for Linux systems that use
init.d
:
# service asperanoded restart
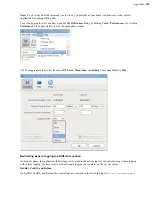
Setting the host key path:
To set the SSH host key path instead of the fingerprint, from which the fingerprint will
be extracted automatically, run the following command:
# asconfigurator -x "set_server_data;ssh_host_key_path,
ssh_key_filepath
"
This command creates a line similar to the following in the
<server>
section of
aspera.conf
:
<ssh_host_key_path>/etc/ssh/ssh_host_rsa_key.pub
</ssh_host_key_path>
Restart the node service to activate your changes, as described for "Retreiving and setting the host key
fingerprint".
8.
Install properly signed SSL certificates.
Though your Aspera server automatically generates self-signed certificates, Aspera recommends installing valid,
signed certificates. These are required for some applications.
Securing Content in your Workflow
1.
If your workflow allows, enable server-side encryption-at-rest (EAR).
When files are uploaded from an Aspera client to the Aspera server, server-side encryption-at-rest (EAR) saves
files on disk in an encrypted state. When downloaded from the server, server-side EAR first decrypts files
automatically, and then the transferred files are written to the client's disk in an unencrypted state. Server-side
EAR provides the following advantages:
• It protects files against attackers who might gain access to server-side storage. This is important primarily
when using NAS storage or cloud storage, where the storage can be accessed directly (and not just through the
computer running HST Server).
• It is especially suited for cases where the server is used as a temporary location, such as when one client
uploads a file and another client downloads it.
• Server-side EAR can be used together with client-side EAR. When used together, content is doubly encrypted.
• Server-side EAR doesn't create an "envelope" as client-side EAR does. The transferred file stays the same
size as the original file. The server stores the metadata necessary for server-side EAR separately in a file of
the same name with the file extension
.aspera-meta
. By contrast, client-side EAR creates a envelope file