| Appendix |
343
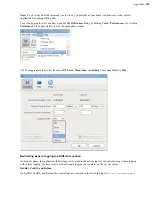
GUI:
Go to
Connections >
connection_name
> Security
. Select
Encrypt uploaded files with a password
and
set the password. Select
Decrypt password-protected files downloaded
and enter the password.
Ascp command line:
Set the encryption and decryption password as the environment variable
ASPERA_SCP_FILEPASS
. For uploads (
--mode=send
), use
--file-crypt=encrypt
. For downloads
(
--mode=recv
), use
--file-crypt=decrypt
.
Note:
When a transfer to HST Server falls back to HTTP or HTTPS, client-side EAR is no longer supported.
If HTTP fallback occurs while uploading, then the files are NOT encrypted. If HTTP fallback occurs while
downloading, then the files remain encrypted.
Server configuration
To configure the server to require client-side EAR and to require strong content protection passwords, run the
following commands:
# asconfigurator -x "set_node_data;transfer_encryption_content_protection_required,true"
# asconfigurator -x "set_node_data;transfer_encryption_content_protection_strong_pass_required,true"
Note:
These commands set the global configuration. Depending on your work flow, you might want to require
client-side EAR and strong passwords for only specific users or groups.
5.
For particularly sensitive content, do not store unecrypted content on any computer with network access.
HST Server, HST Endpoint, and Desktop Client include the
asprotect
and
asunprotect
command-line
tools that can be used to encrypt and decrypt files. Use an external drive to physically move encrypted files
between a network-connected computer and an unconnected computer on which the files can be unencrypted.
• To encrypt a file before moving it to a computer with network access, run the following commands to set the
encryption password and encrypt the file:
# export ASPERA_SCP_FILEPASS=
password
# /opt/aspera/bin/asprotect -o
filename
.aspera-env
filename
• To download client-side-encrypted files without decrypting them immediately, run the transfer without
decryption enabled (clear
Decrypt password-protected files downloaded
in the GUI or do not specify
--
file-crypt=decrypt
on the
ascp
command line).
• To decrypt encrypted files, run the following commands to set the encryption password and decrypt the file:
# export ASPERA_SCP_FILEPASS=
password
# /opt/aspera/bin/asprotect -o
filename
filename
.aspera-env
Testing and Optimizing Transfer Performance
To verify that your system's FASP transfer is reaching the target rate and can use the maximum bandwidth capacity,
prepare a client to connect to an Aspera server. For these tests, you can transfer an existing file or file set, or you can
transfer uninitialized data in place of a source file, which you can destroy at the destination, eliminating the need to
read from or write to disk and saving disk space.
Using faux:/// as a Test Source or Destination
You can use
faux:///
as the argument for the source or destination of an Ascp session to test data transfer without
reading from disk on the source and writing to disk on the target. The argument takes different syntax depending on if
you are using it as a mock source file or mock source directory.
Note:
If you set very large file sizes (> PB) in a
faux:///
source, Aspera recommends that you use
faux://
as a
target on the destination because most computers do not have enough system memory available to handle files of this
size and your transfer might fail.
Faux Source File