| Configure the Server from the Command Line |
54
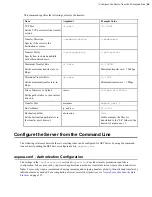
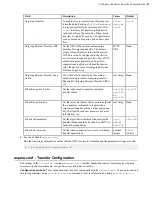
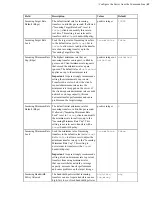
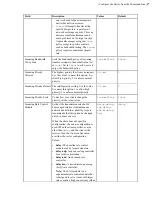
Field
Description
Values
Default
the setting. These settings use the CFB
or GCM mode depending on the client
version and cipher requested. Supports
all client versions.
•
aes-128-cfb
,
aes-192-cfb
, or
aes-256-cfb
- require that transfers
use the CFB encryption mode and a
cipher key that is as long or longer than
the setting. Supports all client versions.
•
aes-128-gcm
,
aes-192-gcm
,
or
aes-256-gcm
- require that
transfers use the GCM encryption
mode introduced in version 3.9.0 and a
cipher that is as long or longer than the
setting.
Do encrypted transfers
in FIPS-140-2-certified
encryption mode
Set to
true
for
ascp
to use a FIPS
140-2-certified encryption module. When
enabled, transfer start is delayed while the
FIPS module is verified.
When you run
ascp
in FIPS mode (that
is,
<fips_enabled>
is set to
true
in
aspera.conf
), and you use passphrase-
protected SSH keys, you must use keys
generated by running
ssh-keygen
in a
FIPS-enabled system, or convert existing
keys to a FIPS-compatible format using a
command such as the following:
openssl pkcs8 -topk8 -
v2 aes128 -in
id_rsa
-
out
new-id_rsa
Important:
When set to
true
, all ciphers
and hash algorithms that are not FIPS
compliant will abort transfers.
true
or
false
false
Bind IP Address
Specify an IP address for server-side
ascp
to bind its UDP connection. If a
valid IP address is given,
ascp
sends and
receives UDP packets only on the interface
corresponding to that IP address.
Important:
The bind address should
only be modified (changed to an address
other than 127.0.0.1) if you, as the System
Administrator, understand the security
ramifications of doing so, and have
undertaken precautions to secure the SOAP
service.
valid IPv4 address None specified
Bind UDP Port
Prevent the client-side
ascp
process from
using the specified UDP port.
integer between 1
and 65535
33001