| Appendix |
335
Docroot
File Restriction
How to set
See
on
page 33.
See
on page 164.
URL Encoding Characters
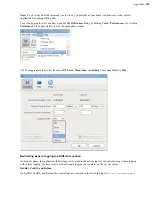
The following reserved characters are often included in passwords and secret keys:
Character
!
#
$
&
'
(
)
*
+
URL
encoded
%21
%23
%24
%26
%27
%28
%29
%2A
%2B
Character
.
/
:
;
=
?
@
[
]
URL
encoded
%2C
%2F
%3A
%3B
%3D
%3F
%40
%5B
%5D
To URL encode other characters and to encode entire strings at once, you may use the online tool:
http://www.url-encode-decode.com/
Select
UTF-8
as the target.
Aspera Ecosystem Security Best Practices
Your Aspera applications can be configured to maximize system and content security. The following sections describe
the recommended settings and practices that best protect your content when using IBM Aspera High-Speed Transfer
Server and IBM Aspera High-Speed Transfer Endpoint.
Contents
Securing the Systems that Run Aspera Software
Securing the Aspera Application
Securing Content in your Workflow
Securing the Systems that Run Aspera Software
The systems that run Aspera software can be secured by keeping them up to date, by applying security fixes, and by
configuring them using the recommended settings.
Updates
Aspera continually improves the built-in security of its products, as do the producers of third-party components used
by Aspera, such as Apache, Nginx, and OpenSSH. One of the first lines of defense is keeping your products up to
date to ensure that you are using versions with the latest security upgrades:
• Keep your operating system up to date.
• Keep your Aspera products up to date.
• If using, keep OpenSSH up to date. The server security instructions require that OpenSSH 4.4 or newer (Aspera
recommends 5.2 or newer) is installed on your system in order to use the
Match
directive.
Match
allows you
to selectively override certain configuration options when specific criteria (based on user, group, hostname, or
address) are met.
• If you are using the HST Server web UI, keep Apache server up to date.
Security Fixes