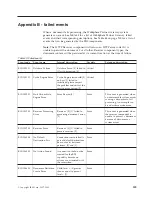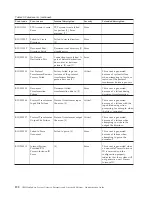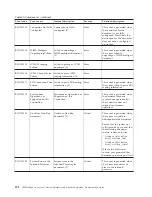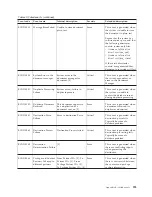
The validity status of the certificate can be found in the WebSphere Partner
Gateway Console. The WebSphere Partner Gateway Console displays the validity
period of certificates on the Certificate List page. The validity period is shown in
red if the certificate is expired.
If the CA certificate is expired, obtain a new certificate from the CA that issued the
certificate. This new CA certificate should be uploaded in WebSphere Partner
Gateway Console.
Note:
If the uploaded certificate is a self signed certificate for Server authentication
and has expired, then the certificate is disabled in the WebSphere Partner Gateway
Console.
VCBaseException in the SystemOut.log
When there is an exception while configuring the hub using the console, the
Console log shows the exception also as part of logging information. For example,
if you try to create an interaction that already exists, you will receive the
VCBaseException in the
SystemOut.log
file. This exception is acceptable as part of
Logging.
Reporting file size for documents greater than 2 GB
When a document is greater than 2 GB in size, WebSphere Partner Gateway might
show the file length as 0 KB in the document viewer. This is because of a
maximum limit for the database datatype.
SSL handshake fails because no certificate received
This problem occurs during the SSLHandShake between a partner and WebSphere
Partner Gateway when you are sending to a partner using SSL with Client
Authentication. If the partner does not send the list of certifying authority
certificates, the SSL client in WebSphere Partner Gateway does not send the client
certificate. This causes the handshake failure.
To resolve the handshake failure, you modify the
java.security
file in WebSphere
Application Server installations. This file is located in the
<
WAS installation
directory
>\java\jre\lib\security
directory.
Note:
For UNIX systems, use the forward slash ( / ) instead of the back slash
( \ ).
The default order of providers in the
java.security
file is as follows:
security.provider.1=com.ibm.crypto.provider.IBMJCE
security.provider.2=com.ibm.jsse.IBMJSSEProvider
security.provider.3=com.ibm.jsse2.IBMJSSEProvider2
security.provider.4=com.ibm.security.jgss.IBMJGSSProvider
security.provider.5=com.ibm.security.cert.IBMCertPath
#security.provider.6=com.ibm.crypto.pkcs11.provider.IBMPKCS11
In the
java.security
file, place the IBMJSSE2 provider before the IBMJSSE
provider as shown in the following example.
Note:
If you implement a WebSphere Application Server fix pack after reordering
the
java.security
file, your change is overwritten and the file must be reordered
again.
178
IBM WebSphere Partner Gateway Enterprise and Advanced Editions: Administration Guide
Summary of Contents for E02HRLL-G - WebSphere Partner Gateway...
Page 20: ...14 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 66: ...60 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 80: ...74 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 86: ...80 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 90: ...84 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 134: ...128 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 154: ...148 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 194: ...188 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 228: ...222 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 258: ...252 IBM WebSphere Partner Gateway Enterprise and Advanced Editions Administration Guide...
Page 267: ......
Page 268: ...Printed in USA...