220
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
Cisco Secure ACS uses the certificate store that is built into the Windows
operating system. The server certificate may be installed in several ways.
If you have an external public/private CA, you can add the CA to the local
certificate storage on the ACS. After the certificate has been added, it must be
enabled on the certificate trust list before it can be used to authenticate users.
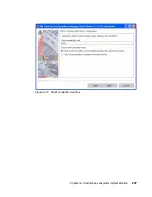
Cisco Secure ACS Version 4.0 can also generate a self-signed certificate. A
self-signed certificate is useful when no CA or other trust authority is required. In
this case, the certificate from Cisco Secure ACS is installed on each client taking
part in the network admission control process.
For the purpose of the book, we used a self-signed certificate.
Using an ACS self-signed certificate
With Cisco Secure ACS Version 4.0 you can generate a self-signed certificate,
which is useful when no CA or other trust authority is required.
Note: We highly recommend that you use a production PKI and certificates
signed by the production certificate authority (CA) or a registration authority
(RA) for the most scalable NAC deployments. You will need to use an existing
PKI (internal or outsourced) to securely identify the ACS infrastructure to
endpoint devices (for example, CTA). For information about obtaining and
installing a certificate from a certificate authority refer to (requires CCO login):
http://www.cisco.com/en/US/partner/products/sw/secursw/ps2086/products_user_
guide_chapter09186a008052e963.html
Summary of Contents for Tivoli and Cisco
Page 2: ......
Page 16: ...xiv Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 18: ...xvi Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 20: ...2 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 30: ...12 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 56: ...38 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 94: ...76 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 110: ...92 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 142: ...124 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 225: ...Chapter 6 Compliance subsystem implementation 207 Figure 6 77 Client connection window...
Page 456: ...438 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 458: ...440 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 504: ...486 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 513: ...Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 514: ......
Page 515: ......