404
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
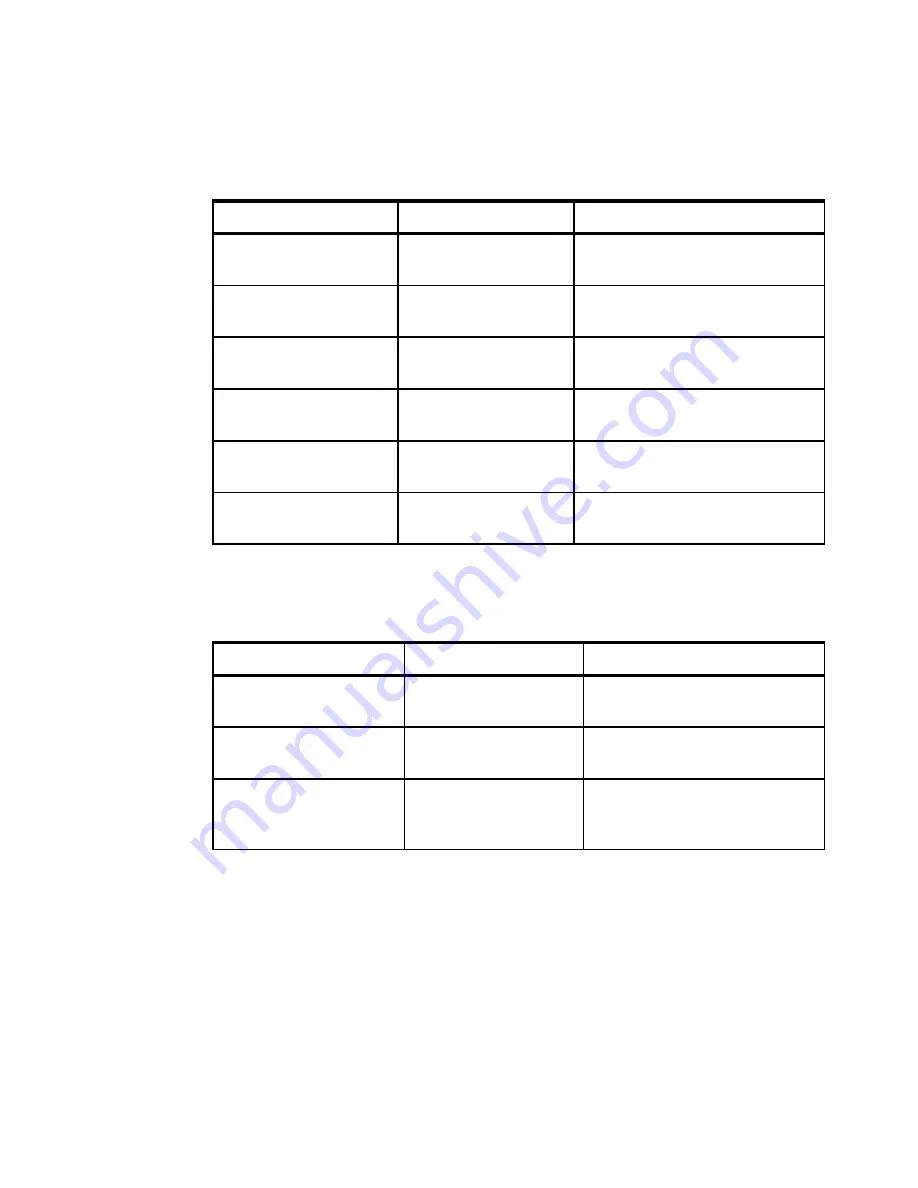
Table 8-5 presents the field names that may be used when a posture item is
selected.
Table 8-5 The field tag usage on posture item level
Table 8-6 presents the field names that may be used when a posture element is
selected.
Table 8-6 The field tag usage on posture element level
The remattribute tag
The remattribute tag is used to access information to the remediation attributes
present in the remediation user interface. These attributes come from various
sources. Some attributes are generated by the Tivoli Security Compliance
Manager client, and the others come from either the local handlers.properties file
or from the HANDLERS_ATTRIBUTES parameter of the policy collector.
Tag
Description
Example
<field:instancename>
Name of the selected
instance.
Symantec Antivirus
<field:instanceid>
Identifier of the
selected instance.
10
<field:collectorname>
Name of the
generating collector.
nac.win.any.nav.PostureNavV2
<field:collectorid>
Identifier of the
generating collector.
36
<field:collectiontime>
Time stamp collection
was performed.
2005-11-10 08:32:06.0
<field:statuscounts>
Status of item's
elements.
{PASS=1, FAIL=2}
Tag
Description
Example
<field:name>
Name of the selected
element
Virus definitions.
<field:status>
Status of the selected
element
FAIL.
<field:msg>
Message associated
with the selected
element
Definitions are out of date.
Summary of Contents for Tivoli and Cisco
Page 2: ......
Page 16: ...xiv Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 18: ...xvi Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 20: ...2 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 30: ...12 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 56: ...38 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 94: ...76 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 110: ...92 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 142: ...124 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 225: ...Chapter 6 Compliance subsystem implementation 207 Figure 6 77 Client connection window...
Page 456: ...438 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 458: ...440 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 504: ...486 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 513: ...Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 514: ......
Page 515: ......
















































