66
Building a Network Access Control Solution with IBM Tivoli and Cisco Systems
Remote offices and branch offices can use the Internet as a primary method
of access or for backup if the primary access method fails.
Organizations can provide partners access over the Internet and exchange
data over VPN.
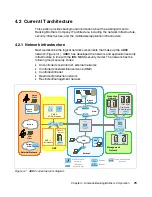
Controlled zone - external network-facing DMZ
One
controlled
, semi-trusted network zone is called the DMZ. It provides a buffer
zone between the Internet and internal networks. This zone can realize the
following benefits:
DMZ can terminate partner traffic or any other WAN traffic before it enters any
restricted production zone.
This zone terminates all dial-up users and VPN traffic.
The Tivoli Configuration Manager Web Gateway is typically located in the
DMZ.
Controlled zone - intranet
The intranet is the other
controlled
zone. Local client users on the LAN
infrastructure and remote office users, using WAN-technologies to connect to
various enterprise resources, are participants of this zone.
Restricted zone - production network
One or more network zones may be designated as
restricted
zones in systems to
which access must be strictly controlled. These systems can be production
servers and are typically application servers, database servers, and other
servers that support business-critical functions. Direct access to these systems
from uncontrolled networks should not be permitted. The Security Compliance
Manager server, Security Compliance Manager proxy, and, optionally, the
Configuration Manager Software Distribution server may be placed in the
production network.
Restricted zone - management network
This zone contains network and enterprise management systems. The ACS can
typically be part of the management zone.
Other networks
The network examples that we use do not necessarily include all possible
scenarios. There are organizations that extensively segment functions into
various subnetworks. However, in general, the principles discussed here may be
translated easily into appropriate architectures for such environments.
Summary of Contents for Tivoli and Cisco
Page 2: ......
Page 16: ...xiv Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 18: ...xvi Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 20: ...2 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 30: ...12 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 56: ...38 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 94: ...76 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 110: ...92 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 142: ...124 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 225: ...Chapter 6 Compliance subsystem implementation 207 Figure 6 77 Client connection window...
Page 456: ...438 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 458: ...440 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 504: ...486 Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 513: ...Building a Network Access Control Solution with IBM Tivoli and Cisco Systems...
Page 514: ......
Page 515: ......