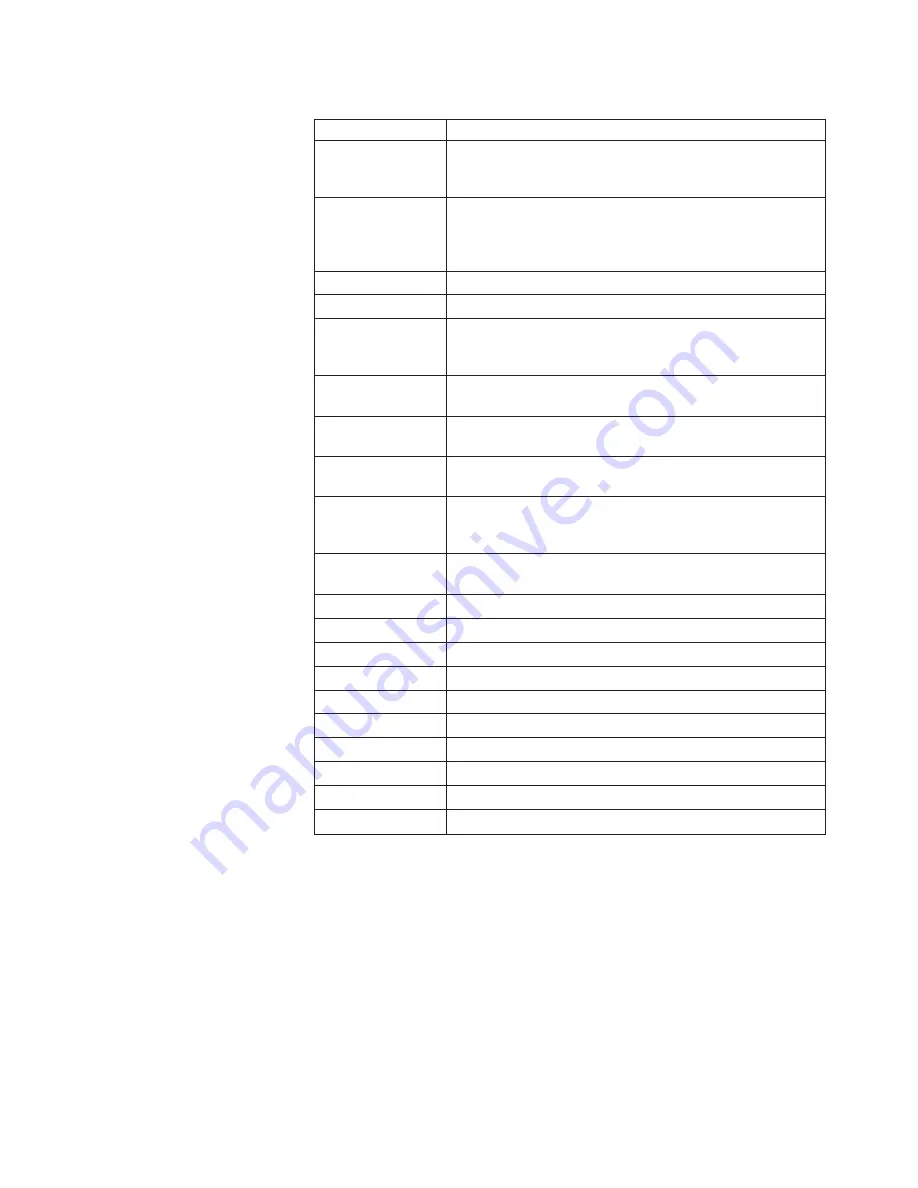
Table 5. Available algorithm keywords for the cipher string (continued)
Algorithm keyword Meaning
eNULL
or
NULL
NULL ciphers offer no encryption at all and are a security
risk. These cipher suites are disabled unless explicitly
included.
aNULL
The cipher suites offering no authentication. This is
currently the anonymous DH algorithms. These cipher suites
are vulnerable to
man-in-the-middle
attacks. Use is normally
discouraged.
kRSA
and
RSA
Cipher suites using RSA key exchange.
kEDH
Cipher suites using ephemeral DH key agreement.
kDHr
and
kDHd
Cipher suites using DH key agreement and DH certificates
signed by Certificate Authorities with RSA and DSS keys
respectively. Not implemented.
aRSA
Cipher suites using RSA authentication. This is, the
certificates carry RSA keys.
aDSS
and
DSS
Cipher suites using DSS authentication. This is, the
certificates carry DSS keys.
aDH
Cipher suites effectively using DH authentication. This is,
the certificates carry DH keys. Not implemented.
kFZA
,
aFZA
,
eFZA
or,
FZA
Cipher suites using FORTEZZA key exchange,
authentication, encryption, or all FORTEZZA algorithms.
Not implemented.
TLSv1
,
SSLv3
, and
SSLv2
TLS version 1.0, SSL version 3.0, and SSL version 2.0 cipher
suites, respectively.
DH
Cipher suites using DH, including anonymous DH.
ADH
Anonymous DH cipher suites.
3DES
Cipher suites using triple DES.
DES
Cipher suites using DES, except triple DES.
RC4
Cipher suites using RC4.
RC2
Cipher suites using RC2.
IDEA
Cipher suites using IDEA.
MD5
Cipher suites using MD5.
SHA1
or
SHA
Cipher suites using SHA-1.
AES
Cipher suites using AES.
The cipher string consists of one or more cipher keywords separated by
colons. Commas or spaces are acceptable separators, but colons are the
norm.
The cipher string can take different forms.
v
A single cipher suite, such as
RC4-SHA
.
v
A list of cipher suites that contains a certain algorithm, or cipher suites
of a certain type. For example
SHA1
represents all ciphers suites using the
SHA-1 digest algorithm.
v
A combination of single cipher string using the
+
character, which is
used as a logical
AND
operation. For example
SHA1+DES
represents all
cipher suites that contain the SHA-1 and the DES algorithms.
Chapter 11. Crypto configuration mode
233
Summary of Contents for WebSphere XS40
Page 1: ...WebSphere DataPower XML Security Gateway XS40 Command Reference Version 3 7 2 ...
Page 2: ......
Page 3: ...WebSphere DataPower XML Security Gateway XS40 Command Reference Version 3 7 2 ...
Page 44: ...18 Command Reference ...
Page 194: ...168 Command Reference ...
Page 198: ...172 Command Reference ...
Page 206: ...180 Command Reference ...
Page 210: ...184 Command Reference ...
Page 222: ...196 Command Reference ...
Page 232: ...206 Command Reference ...
Page 238: ...212 Command Reference ...
Page 268: ...242 Command Reference ...
Page 272: ...246 Command Reference ...
Page 276: ...250 Command Reference ...
Page 288: ...262 Command Reference ...
Page 292: ...266 Command Reference ...
Page 298: ...272 Command Reference ...
Page 320: ...294 Command Reference ...
Page 322: ...296 Command Reference ...
Page 340: ...314 Command Reference ...
Page 344: ...318 Command Reference ...
Page 352: ...326 Command Reference ...
Page 360: ...334 Command Reference ...
Page 368: ...342 Command Reference ...
Page 376: ...350 Command Reference ...
Page 386: ...360 Command Reference ...
Page 392: ...366 Command Reference ...
Page 396: ...370 Command Reference ...
Page 402: ...376 Command Reference ...
Page 404: ...378 Command Reference ...
Page 408: ...382 Command Reference ...
Page 446: ...420 Command Reference ...
Page 450: ...424 Command Reference ...
Page 456: ...430 Command Reference ...
Page 520: ...494 Command Reference ...
Page 536: ...510 Command Reference ...
Page 550: ...524 Command Reference ...
Page 584: ...558 Command Reference ...
Page 600: ...574 Command Reference ...
Page 605: ... timeout 500 Chapter 63 RADIUS configuration mode 579 ...
Page 606: ...580 Command Reference ...
Page 650: ...624 Command Reference ...
Page 668: ...642 Command Reference ...
Page 704: ...678 Command Reference ...
Page 714: ...688 Command Reference ...
Page 726: ...700 Command Reference ...
Page 734: ...708 Command Reference ...
Page 752: ...726 Command Reference ...
Page 756: ...730 Command Reference ...
Page 804: ...778 Command Reference ...
Page 880: ...854 Command Reference ...
Page 892: ...866 Command Reference ...
Page 912: ...886 Command Reference ...
Page 918: ...892 Command Reference ...
Page 940: ...914 Command Reference ...
Page 946: ...920 Command Reference ...
Page 974: ...948 Command Reference ...
Page 1004: ...978 Command Reference ...
Page 1030: ...1004 Command Reference ...
Page 1032: ...1006 Command Reference ...
Page 1065: ......
Page 1066: ... Printed in USA ...
















































