IDEMIA DOCUMENT
– REPRODUCTION AND DISCLOSURE PROHIBITED
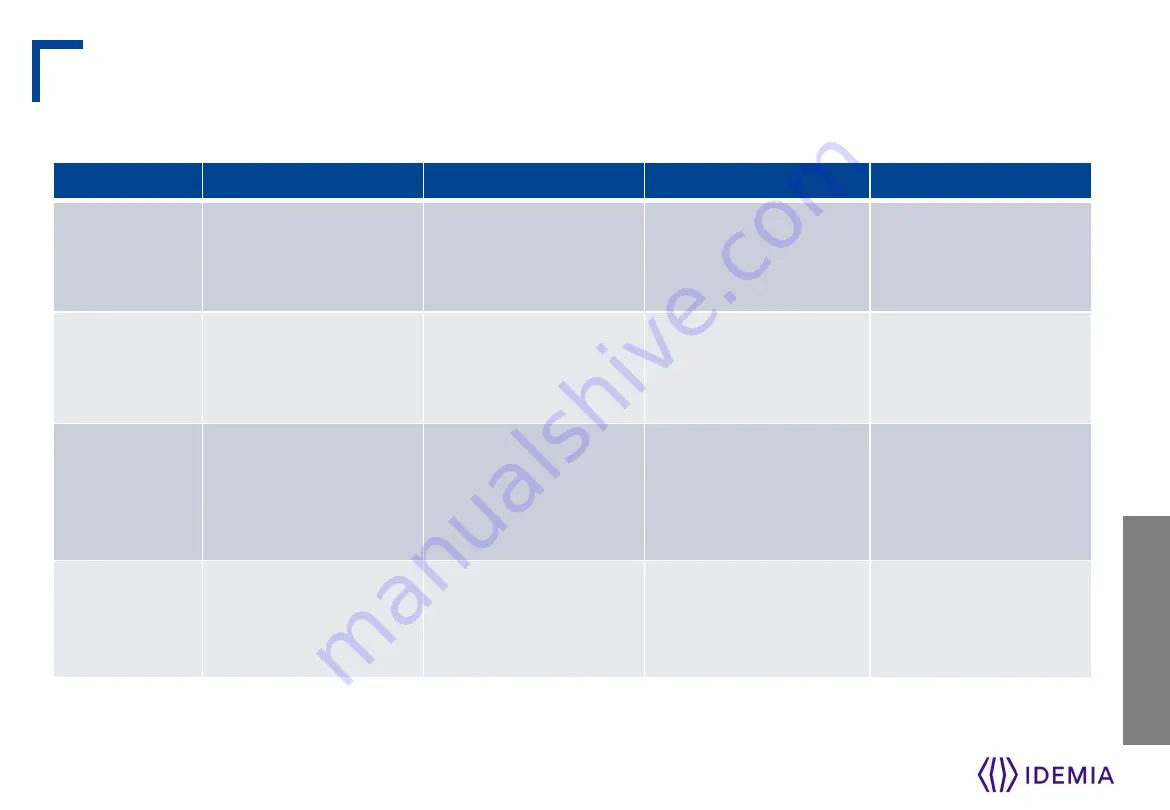
The terminal can be configured in one of the modes described in the table below
Access Control Modes
8
Identification
Authentication
Multifactor
Proxy
Access
control
application
Application that runs
on the terminal when
it starts.
Application that runs
on the terminal when
it starts.
Application that runs
on the terminal when
it starts.
Remote application
that controls the
terminal through
network commands
Access
control
triggering
event
A user swipes his/her
hand in the biometric
sensor.
A user places a
contactless card in
front of the reader.
(*)
Both Identification
and Authentication
triggers are enabled.
Triggering events are
selected by the
remote application
Biometric
check (if
enabled)
The user’s captured
fingerprints are
matched against all
fingerprints in the
terminal database.
The user’s captured
fingerprints are
matched against
their reference
fingerprints.
(**)
As per Identification
or Authentication,
depending on the
triggering event
Selected by the
remote application
Decision to
display result
signal to user
By Identification
standalone
application or
controller feedback
By Authentication
standalone
application or
controller feedback
By running
standalone
application or
controller feedback
By remote
application
(* )
or the user enter their Identifier on the keypad, or a Wiegand frame is received from an external device
(**)
stored on the contactless card or in the user record in the terminal’s local database
St
ep
one
:
ov
erv
iew
IDEMIA - 2018_2000035854
– V1









































