InHand ER805 User Manual
24
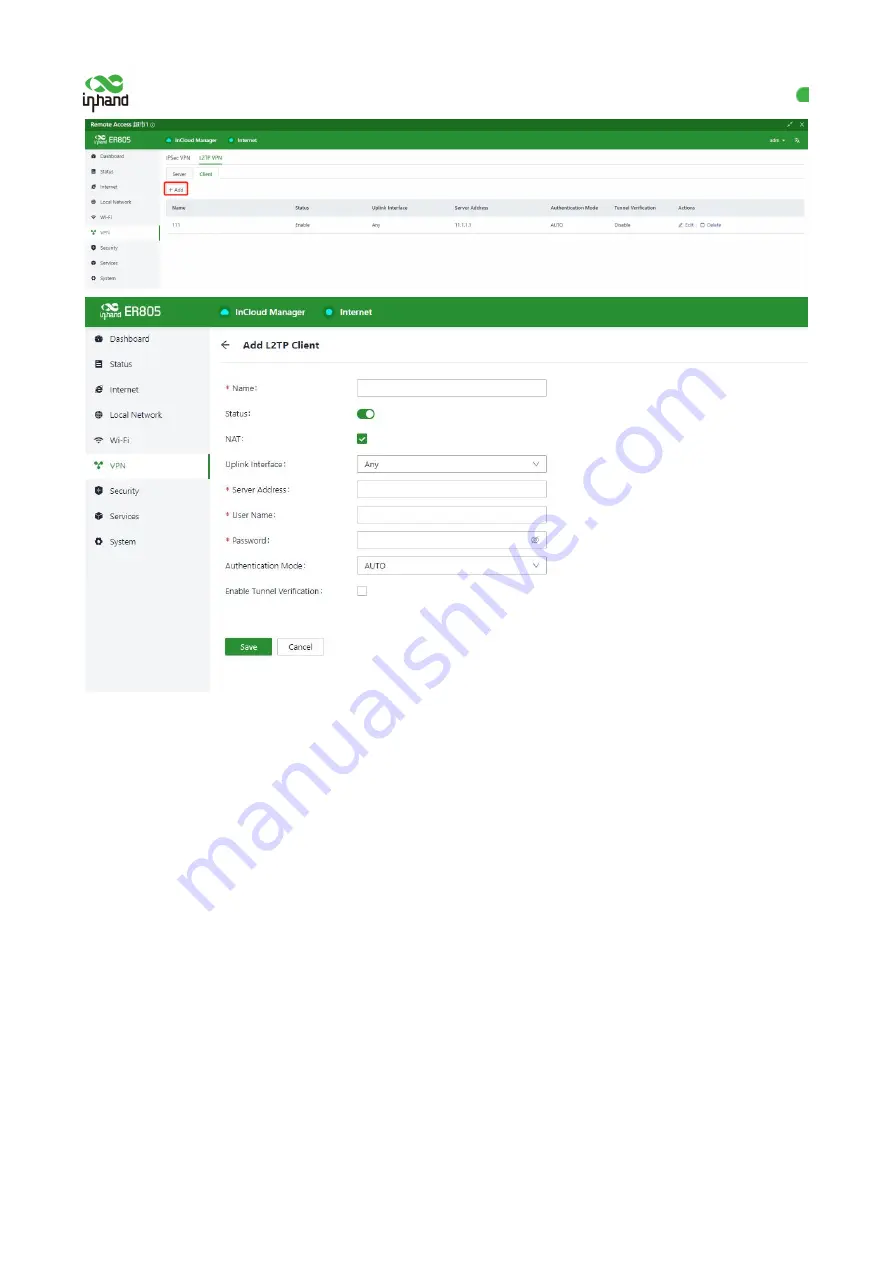
Figure 10-2-1-a/b Adding an L2TP client
Name
: specifies the local identifier of the L2TP client.
Status
: enables or disables L2TP tunneling on the client.
NAT
: enables or disables network address translation (NAT) for packets forwarded by the router for the clients
connected to it.
Uplink Interface
: specifies the uplink interface used to establish a tunnel from the L2TP client to the server.
Server Address
: specifies the IP address used by the remote L2TP server to communicate with the L2TP client.
User Name/Password
: specifies the user name and password for L2TP negotiation, which must be consistent on
both ends of the tunnel.
Authentication
: specifies the authentication mode for the L2TP tunnel.
Enable Tunnel Authentication
: When this option is selected, make sure both ends of the tunnel are configured
with the same server name and verification key.
10.2.2 Server
Generally, an L2TP server is deployed at the headquarters of an enterprise to provide remote access for
employees on the move or in branches. On the
VPN
page, choose
L2TP VPN
>
Server
to display the L2TP
server configuration page.