31
Parameters
Description
Default
Server Address
Server address (domain name / IP)
None
Port
Consistent with the server port
49
Key
Consistent with the server authentication key
None
3.2.4.3 LDAP
One of the great advantages of LDAP is rapid response to users’ searching request. For instance, user’s
authentication which may general a large amount of information sent as the same time. If database is adopted for
this purpose, since it is divided into many tables, each time to meet such a simple requirement, the whole database
has to be searched, integrated and filtered slowly and disadvantageously. LDAP, simple as a table, only requires
username and command and something else. Authentication is met from efficiency and structure.
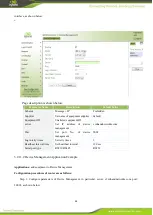
From the left navigation panel, select
Administration << AAA
, then enter “
LDAP
” page, as shown below.
Page description is shown below:
Parameters
Description
Default
Name
Define server name
None
Server Address
Server address (domain name / IP)
None
Port
Consistent with the server port
None
Base DN
The top of LDAP
None
directory tree
Username
Username accessing the server
None
Password
Password accessing the server
None
Security
Encryption mod: None,SSL,StartTLS
None
Verify Peer
Verify Peer
Unopened
3.2.4.4 AAA Settings
AAA supports following authentication ways:
None: with great confidence to users, legal check omitted, generally not recommended.
Local: Have user’s information stored on NAS. Advantages: rapidness, cost reduction. Disadvantages:
storage capacity limited by hardware.
Remote: Have user’s information stored on authentication server. Radius, and LDAP supported