357
4.14.4 LLDP-MED Neighbor
This page provides a status overview for all LLDP-MED neighbors. The displayed table contains a row for each port on which an
LLDP neighbor is detected. The LLDP-MED Neighbor Information screen in
Figure 4-14-3
appears. The columns hold the
following information:
Figure 4-14-3:
LLDP-MED Neighbor Information with no LLDP-MED device detected
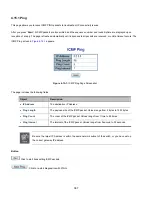
Figure 4-14-4:
LLDP-MED Neighbor Information with LLDP-MED device detected
The page includes the following fields:
Fast start repeat count
Object
Description
Port
The port on which the LLDP frame was received.
Device Type
LLDP-MED Devices are comprised of two primary Device Types: Network
Connectivity Devices and Endpoint Devices.
LLDP-MED Network Connectivity Device Definition
LLDP-MED Network Connectivity Devices, as defined in TIA-1057, provide
access to the IEEE 802 based LAN infrastructure for LLDP-MED Endpoint
Devices. An LLDP-MED Network Connectivity Device is a LAN access device
based on any of the following technologies:
1. LAN Switch/Router
2. IEEE 802.1 Bridge
3. IEEE 802.3 Repeater (included for historical reasons)
4. IEEE 802.11 Wireless Access Point
Summary of Contents for NS4750-24S-4T-4X
Page 1: ...NS4750 24S 4T 4X User Manual P N 1702826 REV 00 01 ISS 14JUL14 ...
Page 56: ...56 Figure 4 2 7 Privilege Levels Configuration Page Screenshot ...
Page 110: ...110 Figure 4 4 6 Mirror Configuration Page Screenshot ...
Page 117: ...117 Figure 4 5 4 LACP Port Configuration Page Screenshot ...
Page 174: ...174 Figure 4 7 10 MST1 MSTI Port Configuration Page Screenshot ...
Page 180: ...180 Figure 4 8 2 Multicast Flooding ...
Page 249: ...249 Figure 4 9 18 Voice VLAN Configuration Page Screenshot ...
Page 271: ...271 Counter Counts the number of frames that match this ACE ...
Page 281: ...281 Figure 4 11 4 Network Access Server Configuration Page Screenshot ...
Page 315: ...315 ...
Page 328: ...328 ...
Page 335: ...335 ...
Page 346: ...346 Figure 4 14 1 LLDP Configuration Page Screenshot ...
Page 350: ...350 Figure 4 14 2 LLDP MED Configuration Page Screenshot ...
Page 372: ...372 Figure 4 16 1 Loop Protection Configuration Page Screenshot ...