374
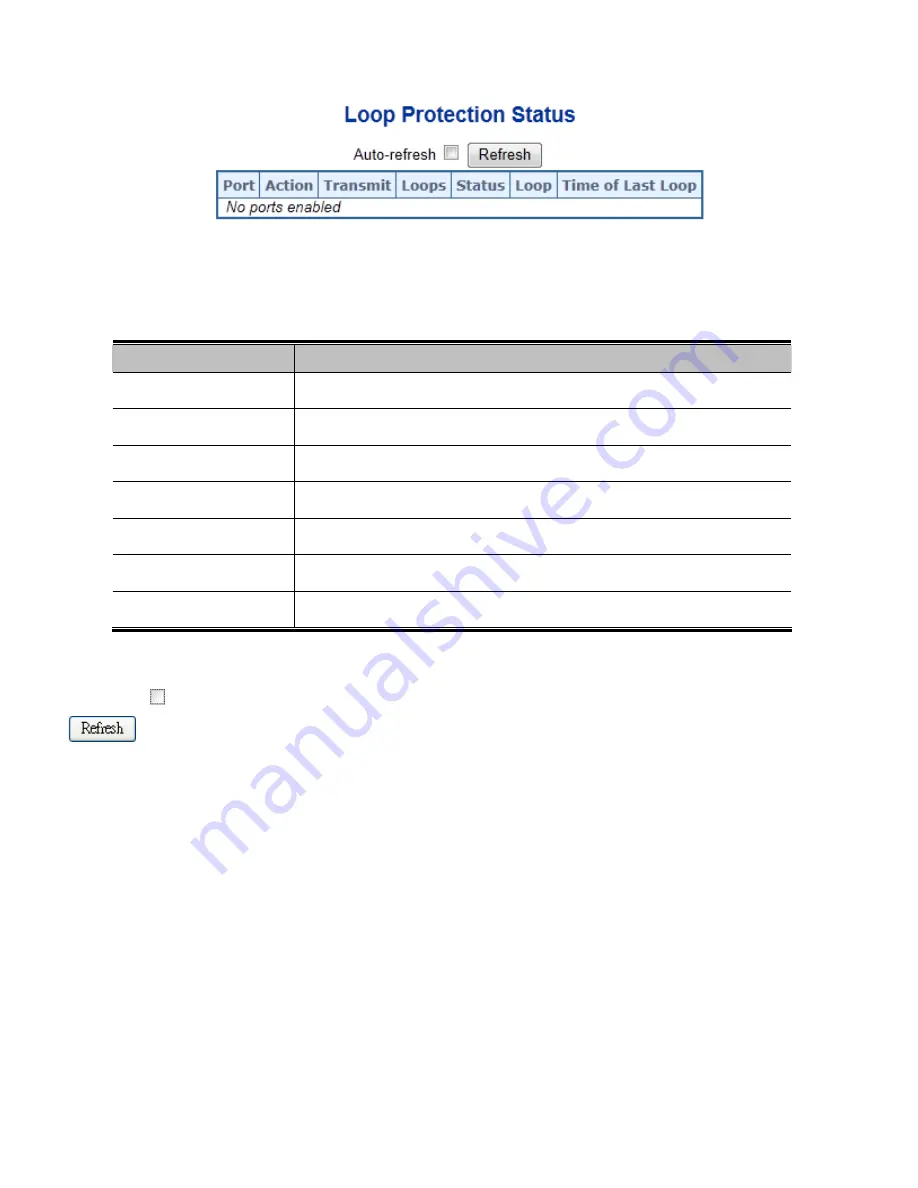
Figure 4-16-2:
Loop Protection Status Page Screenshot
The page includes the following fields:
Object
Description
Port
The switch port number of the logical port.
Action
The currently configured port action.
Transmit
The currently configured port transmit mode.
Loops
The number of loops detected on this port.
Status
The current loop protection status of the port.
Loop
Whether a loop is currently detected on the port.
Time of Last Loop
The time of the last loop event detected.
Buttons
Auto-refresh
: Check this box to refresh the page automatically. Automatic refresh occurs every 3 seconds.
: Click to refresh the page immediately.
Summary of Contents for NS4750-24S-4T-4X
Page 1: ...NS4750 24S 4T 4X User Manual P N 1702826 REV 00 01 ISS 14JUL14 ...
Page 56: ...56 Figure 4 2 7 Privilege Levels Configuration Page Screenshot ...
Page 110: ...110 Figure 4 4 6 Mirror Configuration Page Screenshot ...
Page 117: ...117 Figure 4 5 4 LACP Port Configuration Page Screenshot ...
Page 174: ...174 Figure 4 7 10 MST1 MSTI Port Configuration Page Screenshot ...
Page 180: ...180 Figure 4 8 2 Multicast Flooding ...
Page 249: ...249 Figure 4 9 18 Voice VLAN Configuration Page Screenshot ...
Page 271: ...271 Counter Counts the number of frames that match this ACE ...
Page 281: ...281 Figure 4 11 4 Network Access Server Configuration Page Screenshot ...
Page 315: ...315 ...
Page 328: ...328 ...
Page 335: ...335 ...
Page 346: ...346 Figure 4 14 1 LLDP Configuration Page Screenshot ...
Page 350: ...350 Figure 4 14 2 LLDP MED Configuration Page Screenshot ...
Page 372: ...372 Figure 4 16 1 Loop Protection Configuration Page Screenshot ...