Security Target
Version 1.1
2022-03-08
30
5.5.1.2
Sub‐Protocol Rules (DVI‐I Protocol) (D Models) (FDP_SPR_EXT.1/DVI
-I(D))
FDP_SPR_EXT.1.1/DVI-I(D)
The TSF shall apply the following rules for the [
DVI
‐
I
] protocol:
•
block the following video/display sub‐protocols:
o
[ARC,
o
CEC,
o
EDID from computer to display,
o
HDCP,
o
HEAC,
o
HEC,
o
MCCS]
•
allow the following video/display sub‐protocols:
o
[EDID from display to computer,
o
HPD from display to computer].
5.6
TOE Security Assurance Requirements
The security assurance requirements for the TOE are included by reference from the [PSD].
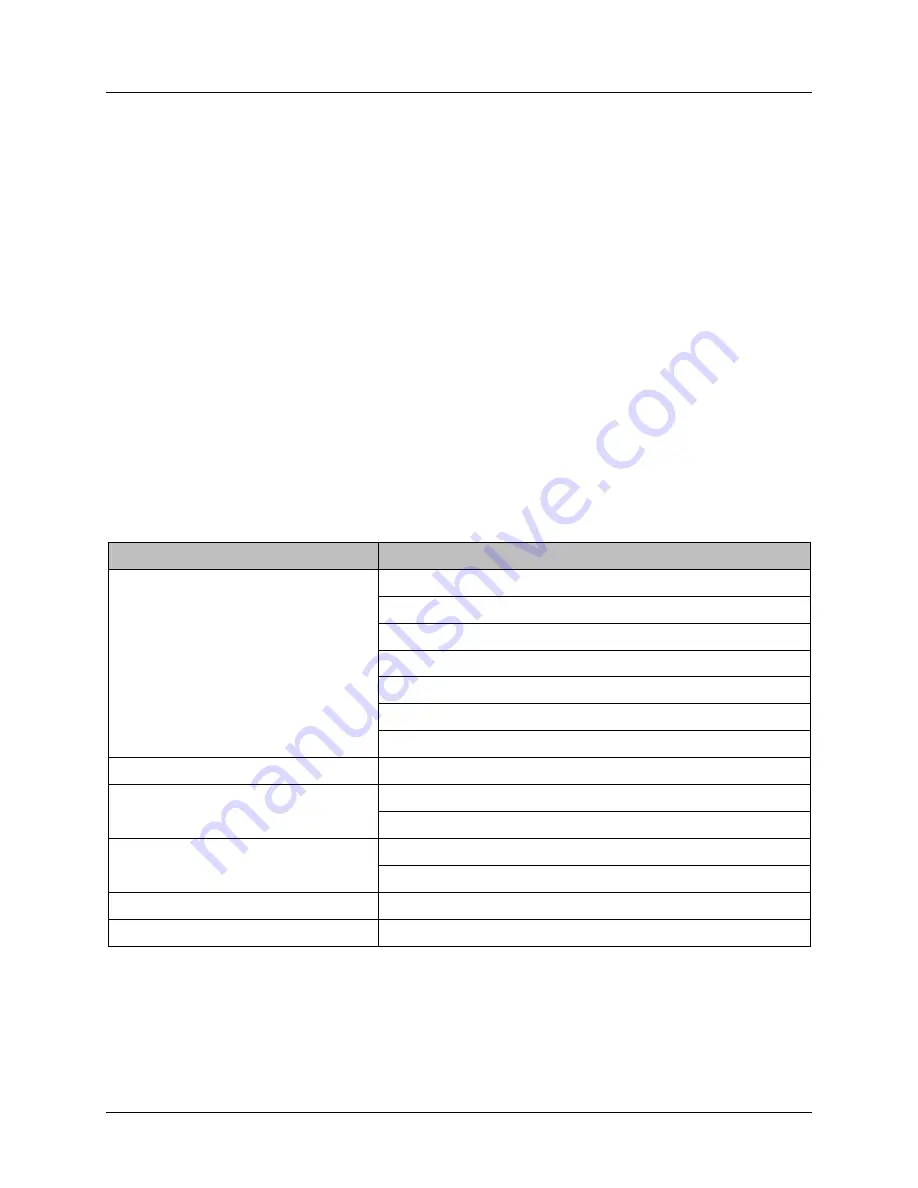
Table 12: Assurance Components
Requirement Class
Requirement Component
Security Target (ASE)
Conformance Claims (ASE_CCL.1)
Extended Components Definition (ASE_ECD.1)
ST Introduction (ASE_INT.1)
Security Objectives (ASE_OBJ.2)
Derived Security Requirements (ASE_REQ.2)
Security Problem Definition (ASE_SPD.1)
TOE Summary Specification (ASE_TSS.1)
Development (ADV)
Basic Functional Specification (ADV_FSP.1)
Guidance Documents (AGD)
Operational User Guidance (AGD_OPE.1)
Preparative Procedures (AGD_PRE.1)
Life Cycle Support (ALC)
Labeling of the TOE (ALC_CMC.1)
TOE CM Coverage (ALC_CMS.1)
Tests (ATE)
Independent Testing
–
Conformance (ATE_IND.1)
Vulnerability Assessment (AVA)
Vulnerability Survey (AVA_VAN.1)