Security Target
Version 1.1
2022-03-08
3
1.3
Conventions
The Security Functional Requirements included in this section are derived from Part 2 of the Common
Criteria for Information Technology Security Evaluation, Version 3.1, Revision 5, with additional extended
functional components.
The CC defines operations on Security Functional Requirements: assignments, selections, assignments
within selections, iterations, and refinements. This document retains all operations completed by the PP
author (i.e. selections/assignments they already filled out). These are formatted as italicized text.
This document uses the following font conventions to identify iterations, extended SFRs and operations
performed by the ST author:
•
Refinement
operation (denoted by
bold text
and underline) is used to add details to a requirement,
and thus further restricts a requirement.
•
Selection
(denoted by italicized
bold
text): is used to select one or more options provided by the
[CC] in stating a requirement. Selection operations completed in the PP are shown in brackets.
•
Assignment
operation (denoted by
bold
text) is used to assign a specific value to an unspecified
parameter, such as the length of a password. Showing the value in square brackets indicates
assignment. Assignments within Selections are denoted by italicized
bold
text).
•
Iteration
operation is identified with a slash (‘/’) and an identifier (e.g. “/KM”).
Additional iterations
made by the ST author are defined with a reference in parentheses to the specific TOE models they
apply to, e.g. “(DP)” indicates the SFR only applies to Disp
layPort models. Though technically not an
iteration FDP_IPC_EXT.1, also uses this convention to clarify that this requirement only applies to
certain models.
•
Extended
SFRs are identified by having a label “EXT” after the SFR name.
1.3.1
Terminology
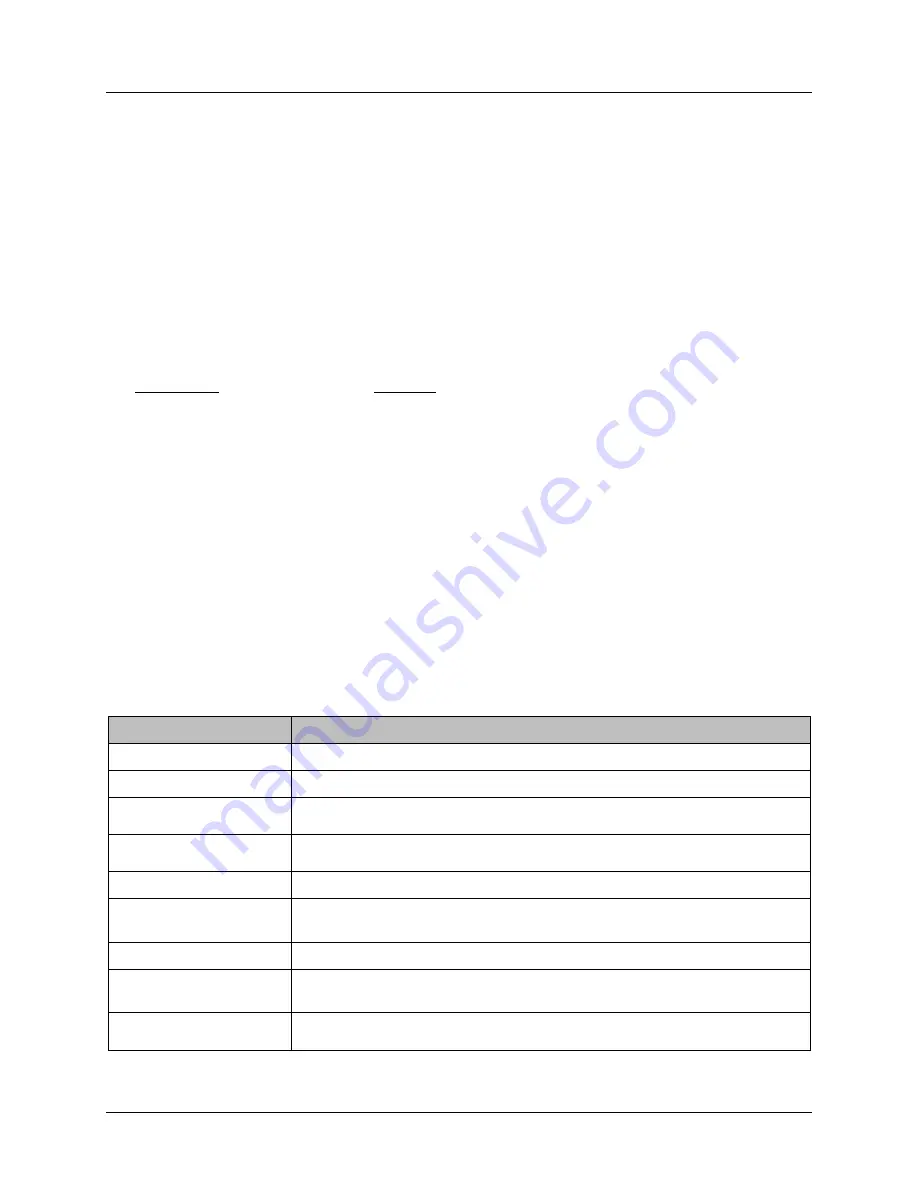
Table 2: Terms and Definitions
Term
Definition
Aligned
Detected and accepted the connection by the KVM.
Assurance
Grounds for confidence that a TOE meets the SFRs.
Authorized Peripheral
A Peripheral Device that is both technically supported and administratively
permitted to have an active interface with the PSD.
Combiner (multi-viewer)
A PSD with video integration functionality that is used to simultaneously display
output from multiple personal computers (PCs).
Common Criteria (CC)
Common Criteria for Information Technology Security Evaluation.
Common Evaluation
Methodology (CEM)
Common Evaluation Methodology for Information Technology Security
Evaluation.
Computer Interface
The PSD’s physical receptacle or port for
connecting to a computer.
Configurable Device
Filtration (CDF)
A PSD function that filters traffic based on properties of a connected peripheral
device and criteria that are configurable by an Administrator.
Connected Computer
A computing device connected to a PSD. May be a personal computer, server,
tablet, or any other computing device.