Security Target
Version 1.1
2022-03-08
10
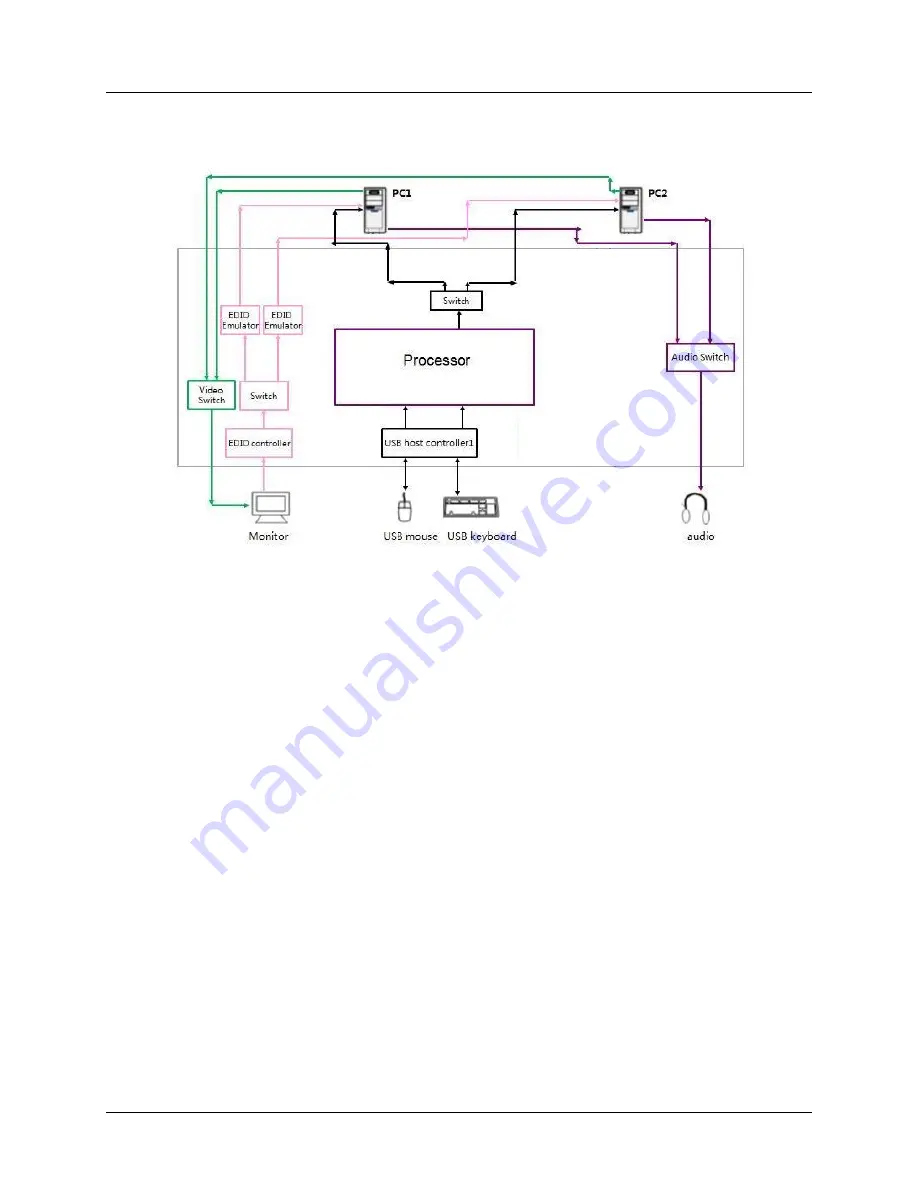
Figure 1: Simplified Block Diagram of a 2-Port KVM TOE
As shown in Figure 1 above, the internal components of the KVM consist of switches, emulators, USB host
controllers, processors, and embedded with non-updateable firmware v1.1.101. The internal hardware
components are identified in Appendix A and include the manufacturer and the part number. The data
flow of USB keyboard/mouse is controlled by the host controller for console HID keyboard and pointing
devices. Details of the data flow architecture are provided in the proprietary Secure KVM Isolation
Document. All keyboard and mouse connections are filtered first, and only authorized devices will be
allowed. The TOE emulates data from authorized USB keyboard and mouse to USB data for computer
sources.
The TOEs proprietary design ensures
there is no possibility of data leakage from a user’s peripheral output
device to the input device; ensures that no unauthorized data flows from the monitor to a connected
computer; and unidirectional buffers ensure that the audio data can travel only from the selected
computer to the audio device. There is no possibility of data leakage between computers or from a
peripheral device connected to a console port to a non-selected computer. Each connected computer has
its own independent Device Controller, power circuit, and EEPROM. Additionally, keyboard and mouse
are always switched together.
All Secure KVM Switch components including the RPS, feature hardware security mechanisms including
tamper-evident labels, always active chassis-intrusion detection, and tamper-proof hardware
construction, while software security includes restricted USB connectivity (non-Human Interface Devices
(HIDs) are ignored when switching), an isolated channel per port that makes it impossible for data to be
communicated between computers, and automatic clearing of the keyboard and mouse buffer.