Security Features for EX Series Switches Overview
Juniper Networks Junos operating system (Junos OS) is a network operating system that
has been hardened through the separation of control forwarding and services planes,
with each function running in protected memory. The control-plane CPU is protected by
rate limiting, routing policy, and firewall filters to ensure switch uptime even under severe
attack. In addition, the switches fully integrate with the Juniper Networks Unified Access
Control (UAC) product to provide both standards-based 802.1X port-level access and
Layer 2 through Layer 4 policy enforcement based on user identity. Access port security
features such as dynamic Address Resolution Protocol (ARP) inspection, DHCP snooping,
and MAC limiting are controlled through a single Junos OS CLI command.
Juniper Networks EX Series Ethernet Switches provide the following hardware and
software security features:
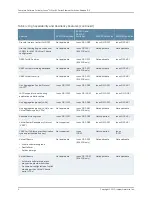
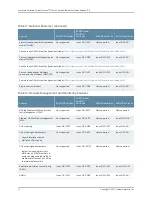
Console Port
—Allows use of the console port to connect to the Routing Engine through
an RJ-45 cable. You then use the command-line interface (CLI) to configure the switch.
Out-of-Band Management
—A dedicated management Ethernet port on the rear panel
allows out-of-band management.
Software Images
—All Junos OS images are signed by Juniper Networks certificate
authority (CA) with public key infrastructure (PKI).
User Authentication, Authorization, and Accounting (AAA)
—Features include:
•
User and group accounts with password encryption and authentication.
•
Access privilege levels configurable for login classes and user templates.
•
RADIUS authentication, authentication, or both, for authenticating users
who attempt to access the switch.
•
Auditing of configuration changes through system logging or RADIUS/.
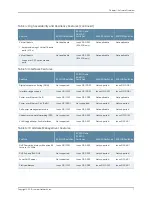
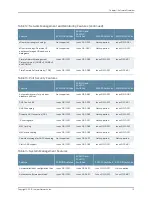
802.1X Authentication
—Provides network access control. Supplicants (hosts) are
authenticated when they initially connect to a LAN. Authenticating supplicants before
they receive an IP address from a DHCP server prevents unauthorized supplicants from
gaining access to the LAN. EX Series switches support Extensible Authentication Protocol
(EAP) methods, including EAP-MD5, EAP-TLS, EAP-TTLS, and EAP-PEAP.
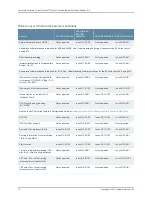
Port Security
—Access port security features include:
•
DHCP snooping—Filters and blocks ingress DHCP server messages on untrusted ports;
builds and maintains an IP-address/MAC-address binding database (called the DHCP
snooping database).
•
Dynamic ARP inspection (DAI)—Prevents ARP spoofing attacks. ARP requests and
replies are compared against entries in the DHCP snooping database, and filtering
decisions are made based on the results of those comparisons.
•
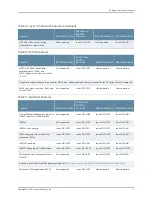
MAC limiting—Protects against flooding of the Ethernet switching table.
Copyright © 2010, Juniper Networks, Inc.
18
Complete Software Guide for Junos
®
OS for EX Series Ethernet Switches, Release 10.3
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...