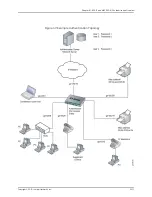
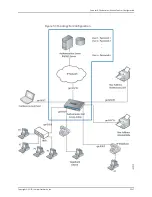
Understanding Guest VLANs for 802.1X on EX Series Switches
Guest VLANs, in conjunction with 802.1X, MAC RADIUS, and captive portal authentication,
provide secure access to the LAN for corporate guests and for end devices that fail the
authentication process.
When a corporate visitor attempts to authenticate on the LAN and authentication fails,
the visitor is moved to a guest VLAN. A guest VLAN typically provides access only to the
Internet.
A guest VLAN can also provide limited access to the LAN in cases when authentication
fails for end devices that are not visitors. When authentication fails, the switch receives
an access-reject message for the end device and determines whether a guest VLAN is
configured on that port. If so, it moves that end device alone to the guest VLAN. If the
access-reject message contains optional VLAN information, then the end device is moved
to the VLAN specified by the RADIUS server and not to the locally configured guest VLAN.
Authentication can fail for many reasons:
•
The end device does not have supplicant software on it (for example, the end device
is a device type that cannot be enabled for 802.1X, such as a printer).
•
The end device provided invalid credentials—a username or password that were not
authenticated by the authentication server.
For end devices that are not 802.1X-enabled, a guest VLAN can allow limited access to
a server from which the non-802.1X-enabled end device can download the supplicant
software and attempt authentication again.
Related
Documentation
Example: Setting Up 802.1X in Conference Rooms to Provide Internet Access to
Corporate Visitors on an EX Series Switch on page 2554
•
•
Understanding Dynamic VLANs for 802.1X on EX Series Switches on page 2537
•
Understanding Authentication on EX Series Switches on page 2526
Copyright © 2010, Juniper Networks, Inc.
2538
Complete Software Guide for Junos
®
OS for EX Series Ethernet Switches, Release 10.3
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...