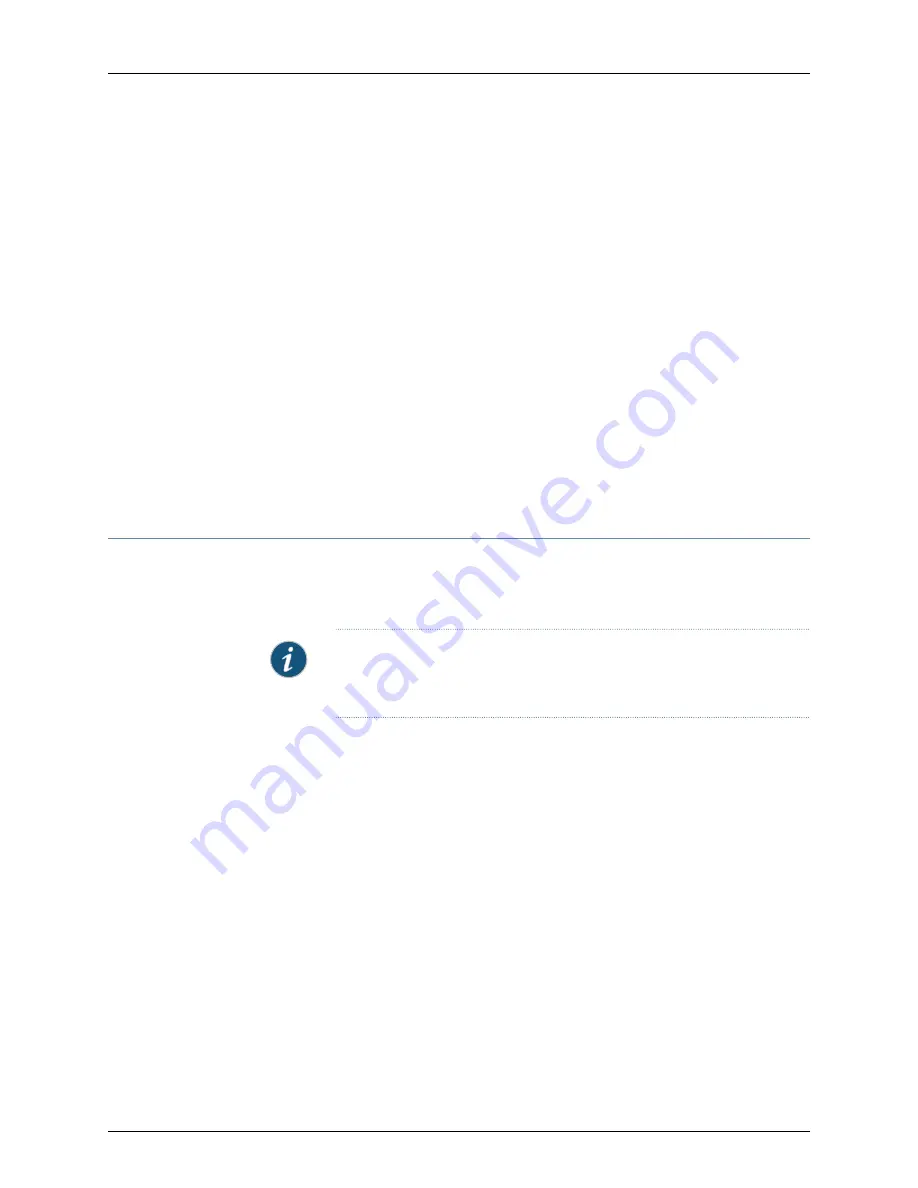
[edit protocols dot1x]
user@switch#
set
authenticator static
00:04:0f:fd:ac:fe
•
Configure a supplicant to bypass authentication if connected through a particular
interface:
[edit protocols dot1x]
user@switch#
set authenticator static 00:04:0f:fd:ac:fe
interface
ge-0/0/5
•
You can configure a supplicant to be moved to a specific VLAN after it is authenticated:
[edit protocols dot1x]
user@switch#
set authenticator static 00:04:0f:fd:ac:fe interface ge-0/0/5
vlan-assignment
default-vlan
Related
Documentation
Example: Configuring Static MAC Bypass of Authentication on an EX Series Switch on
page 2559
•
•
Configuring 802.1X Interface Settings (CLI Procedure) on page 2609
•
Configuring 802.1X Authentication (J-Web Procedure) on page 2610
Configuring MAC RADIUS Authentication (CLI Procedure)
You can permit devices that are not 802.1X-enabled LAN access by configuring MAC
RADIUS authentication on the EX Series switch interfaces to which the hosts are
connected.
NOTE:
You can also allow non-802.1X-enabled devices to access the LAN
by configuring their MAC address for static MAC bypass of authentication.
You can configure MAC RADIUS authentication on an interface that also allows 802.1X
authentication, or you can configure either authentication method alone.
If both MAC RADIUS and 802.1X authentication are enabled on the interface, the switch
first sends the host three EAPOL requests to the host. If there is no response from the
host, the switch sends the host’s MAC address to the RADIUS server to check whether
it is a permitted MAC address. If the MAC address is configured as permitted on the
RADIUS server, the RADIUS server sends a message to the switch that the MAC address
is a permitted address, and the switch opens LAN access to the nonresponsive host on
the interface to which it is connected.
If MAC RADIUS authentication is configured on the interface but 802.1X authentication
is not (by using the
mac-radius restrict
option), the switch attempts to authenticate the
MAC address with the RADIUS server without delaying by attempting 802.1X
authentication first.
Before you configure MAC RADIUS authentication, be sure you have:
2613
Copyright © 2010, Juniper Networks, Inc.
Chapter 83: Configuring Access Control
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...
















































