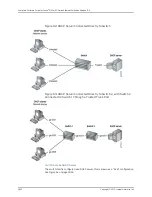
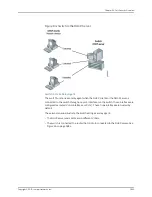
Understanding DAI for Port Security on EX Series Switches
Dynamic ARP inspection (DAI) protects Juniper Networks EX Series Ethernet Switches
against ARP spoofing.
DAI inspects ARP packets on the LAN and uses the information in the DHCP snooping
database on the switch to validate ARP packets and to protect against ARP cache
poisoning. ARP requests and replies are compared against entries in the DHCP snooping
database, and filtering decisions are made based on the results of those comparisons.
When an attacker tries to use a forged ARP packet to spoof an address, the switch
compares the address to entries in the database. If the MAC address or IP address in an
ARP packet does not match a valid entry in the DHCP snooping database, the packet is
dropped.
ARP packets are trapped to the Routing Engine and are rate-limited to protect the switch
from CPU overload.
•
Address Resolution Protocol on page 2836
•
ARP Spoofing on page 2836
•
DAI on EX Series Switches on page 2837
Address Resolution Protocol
Sending IP packets on a multiaccess network requires mapping an IP address to an
Ethernet media access control (MAC) address.
Ethernet LANs use Address Resolution Protocol (ARP) to map MAC addresses to IP
addresses.
The switch maintains this mapping in a cache that it consults when forwarding packets
to network devices. If the ARP cache does not contain an entry for the destination device,
the host (the DHCP client) broadcasts an ARP request for that device's address and
stores the response in the cache.
ARP Spoofing
ARP spoofing (also known as ARP poisoning or ARP cache poisoning) is one way to
initiate man-in-the-middle attacks. The attacker sends an ARP packet that spoofs the
MAC address of another device on the LAN. Instead of the switch sending traffic to the
proper network device, it sends it to the device with the spoofed address that is
impersonating the proper device. If the impersonating device is the attacker's machine,
the attacker receives all the traffic from the switch that should have gone to another
device. The result is that traffic from the switch is misdirected and cannot reach its proper
destination.
One type of ARP spoofing is gratuitous ARP, which is when a network device sends an
ARP request to resolve its own IP address. In normal LAN operation, gratuitous ARP
messages indicate that two devices have the same MAC address. They are also broadcast
when a network interface card (NIC) in a device is changed and the device is rebooted,
so that other devices on the LAN update their ARP caches. In malicious situations, an
Copyright © 2010, Juniper Networks, Inc.
2836
Complete Software Guide for Junos
®
OS for EX Series Ethernet Switches, Release 10.3
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...