•
The IP Source Guard Database on page 2844
•
Typical Uses of Other Junos Operating System (Junos OS) Features with IP Source
Guard on page 2845
IP Address Spoofing
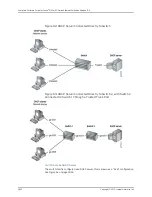
Hosts on access interfaces can spoof source IP addresses and/or source MAC addresses
by flooding the switch with packets containing invalid addresses. Such attacks combined
with other techniques such as TCP SYN flood attacks can result in denial-of-service
(DoS) attacks. With source IP address or source MAC address spoofing, the system
administrator cannot identify the source of the attack. The attacker can spoof addresses
on the same subnet or on a different subnet.
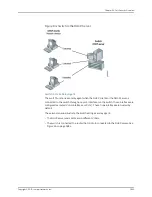
How IP Source Guard Works
IP source guard checks the IP source address and MAC source address in a packet sent
from a host attached to an untrusted access interface on the switch against entries
stored in the DHCP snooping database. If IP source guard determines that the packet
header contains an invalid source IP address or source MAC address, it ensures that the
switch does not forward the packet—that is, the packet is discarded.
When you configure IP source guard, you enable on it on one or more VLANs. IP source
guard applies its checking rules to packets sent from untrusted access interfaces on
those VLANs. By default, on EX Series switches, access interfaces are untrusted and
trunk interfaces are trusted. IP source guard does not check packets that have been sent
to the switch by devices connected to either trunk interfaces or trusted access
interfaces—that is, interfaces configured as
dhcp-trusted
so that a DHCP server can be
connected to that interface to provide dynamic IP addresses.
IP source guard obtains information about IP-address/MAC-address/VLAN bindings
from the DHCP snooping database. It causes the switch to validate incoming IP packets
against the entries in that database.
After the DHCP snooping database has been populated either through dynamic DHCP
snooping or through configuration of specific static IP address/MAC address bindings,
the IP source guard feature builds its database. It then checks incoming packets from
access interfaces on the VLANs on which it is enabled. If the source IP addresses and
source MAC addresses match the IP source guard binding entries, the switch forwards
the packets to their specified destination addresses. If there are no matches, the switch
discards the packets.
The IP Source Guard Database
The IP source guard database looks like this:
user@switch>
show ip-source-guard
IP source guard information:
Interface Tag IP Address MAC Address VLAN
ge-0/0/12.0 0 10.10.10.7 00:30:48:92:A5:9D vlan100
ge-0/0/13.0 0 10.10.10.9 00:30:48:8D:01:3D vlan100
Copyright © 2010, Juniper Networks, Inc.
2844
Complete Software Guide for Junos
®
OS for EX Series Ethernet Switches, Release 10.3
Summary of Contents for JUNOS OS 10.3 - SOFTWARE
Page 325: ...CHAPTER 17 Operational Mode Commands for System Setup 229 Copyright 2010 Juniper Networks Inc ...
Page 1323: ...CHAPTER 56 Operational Mode Commands for Interfaces 1227 Copyright 2010 Juniper Networks Inc ...
Page 2841: ...CHAPTER 86 Operational Commands for 802 1X 2745 Copyright 2010 Juniper Networks Inc ...
Page 3367: ...CHAPTER 113 Operational Mode Commands for CoS 3271 Copyright 2010 Juniper Networks Inc ...
Page 3435: ...CHAPTER 120 Operational Mode Commands for PoE 3339 Copyright 2010 Juniper Networks Inc ...
Page 3529: ...CHAPTER 126 Operational Mode Commands for MPLS 3433 Copyright 2010 Juniper Networks Inc ...