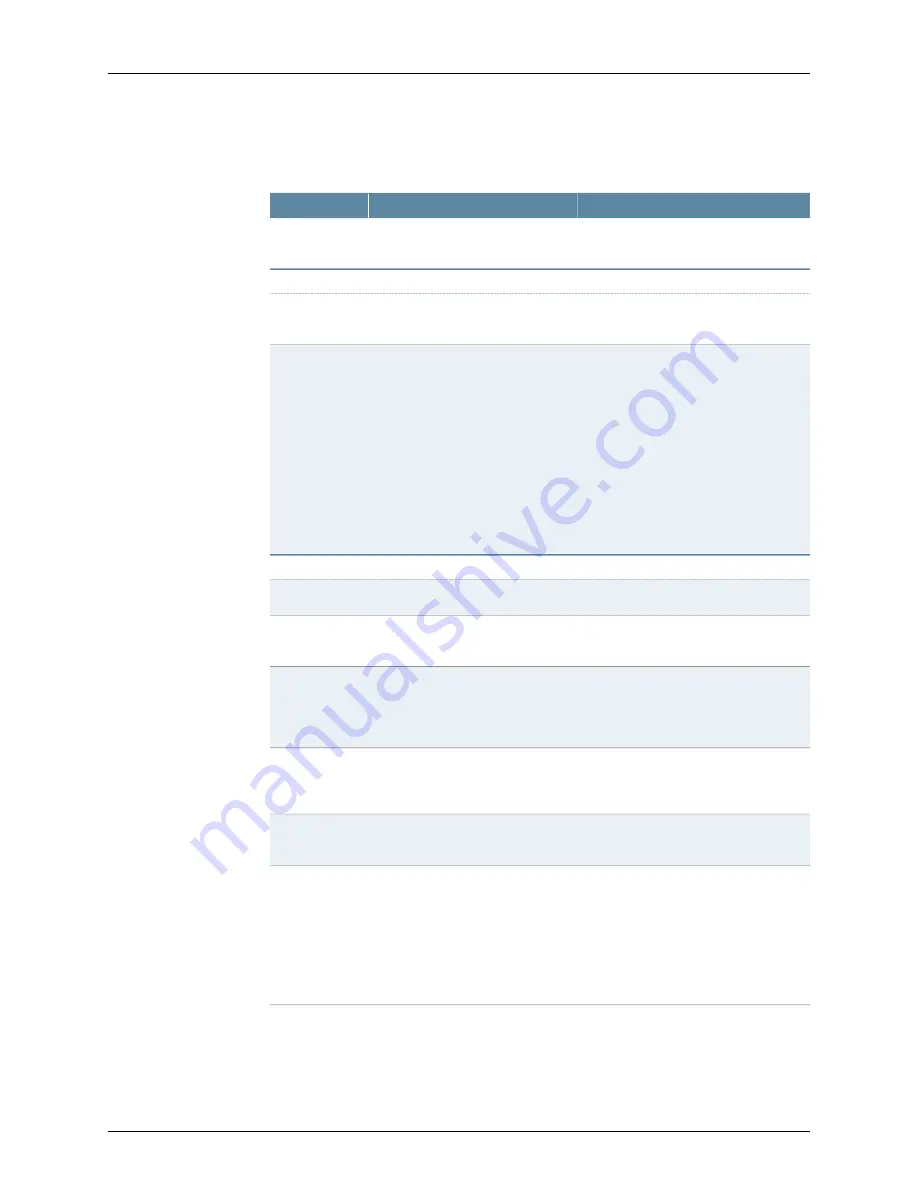
Table 42: Secure Access LDAP Server Instance Configuration
Details
(continued)
Your Action
Function
Option
Enter the password.
Specifies the password for the
admin DN name.
Password
LDAP Settings > Finding User Entries tab
Enter a base DN name. For example,
DC=eng, DC=Juniper, DC=com
.
Starts searching for user entries.
Base DN
Enter a filter value. For example,
entersamAccountname
=
<username>
or cn=
<username>
.
NOTE:
•
Include
<username>
in the filter to
use the username entered on the
sign-in page for the search.
•
Specify a filter that returns 0 or 1 user
DNs per user; the device uses the first
DN returned if more than 1 DN is
returned.
Fine tunes the search.
Filter
LDAP Settings > Determining Group Membership tab
Enter a base DN name.
Starts searching for user groups.
Base DN
Enter a filter value.
Fine tunes the search for a user
group.
Filter
Enter a name if you want to identify all
the members of a static group. For
example, enter
member uniquemember
(iPlanet-specific)
.
Identifies all the members of a static
group.
Member
Attribute
Select
LDAP Settings
>
Determining
Group Membership
>
Reverse group
search
to enable this option.
Starts the search from the member
instead of the group.
Reverse group
search
Enter a name for the query attribute. For
example, enter
memberURL
.
Specifies an LDAP query that returns
the members of a dynamic group.
Query Attribute
Set the number for the search query
time.
Specifies how many levels within a
group to search for the user.
NOTE: The higher the number, the
longer the query time, so we
recommend that you specify to
perform the search no more than
two levels deep.
Nested Group
Level
169
Copyright © 2010, Juniper Networks, Inc.
Chapter 11: Configuring Authentication and Directory Servers
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...
















































