CHAPTER 22
Troubleshooting Secure Access Device
Federated Networks
•
Troubleshooting the IF-MAP Federation Network (NSM Procedure) on page 301
Troubleshooting the IF-MAP Federation Network (NSM Procedure)
Diagnostic tools on the SA Series appliances can assist you with troubleshooting a
federated network.
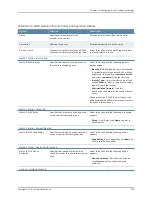
IF-MAP Client User Messages
—On the IF-MAP client, logs the information that is
published and removed from the IF-MAP server.
•
Enable IF-MAP Client User Messages from
Log/Monitoring > User Access > Settings
on the SA Series appliances IF-MAP client.
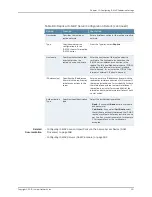
IF-MAP Server Trace
—On the IF-MAP server, logs the XML for all IF-MAP requests and
responses.
•
Enable the IF-MAP Server Trace from
Log/Monitoring > Events > Settings
on the
IF-MAP server.
IF-MAP Server Trace should only be enabled for troubleshooting purposes, as running
this diagnostic incurs a large performance impact.
Related
Documentation
•
Configuring IF-MAP Servers (NSM Procedure) on page 283
•
Configuring IF-MAP Client Settings on the Secure Access Device (NSM Procedure) on
page 284
301
Copyright © 2010, Juniper Networks, Inc.
Summary of Contents for NETWORK AND SECURITY MANAGER
Page 6: ...Copyright 2010 Juniper Networks Inc vi...
Page 12: ...Copyright 2010 Juniper Networks Inc xii Configuring Secure Access Devices Guide...
Page 18: ...Copyright 2010 Juniper Networks Inc xviii Configuring Secure Access Devices Guide...
Page 20: ...Copyright 2010 Juniper Networks Inc 2 Configuring Secure Access Devices Guide...
Page 28: ...Copyright 2010 Juniper Networks Inc 10 Configuring Secure Access Devices Guide...
Page 40: ...Copyright 2010 Juniper Networks Inc 22 Configuring Secure Access Devices Guide...
Page 46: ...Copyright 2010 Juniper Networks Inc 28 Configuring Secure Access Devices Guide...
Page 50: ...Copyright 2010 Juniper Networks Inc 32 Configuring Secure Access Devices Guide...
Page 52: ...Copyright 2010 Juniper Networks Inc 34 Configuring Secure Access Devices Guide...
Page 82: ...Copyright 2010 Juniper Networks Inc 64 Configuring Secure Access Devices Guide...
Page 110: ...Copyright 2010 Juniper Networks Inc 92 Configuring Secure Access Devices Guide...
Page 154: ...Copyright 2010 Juniper Networks Inc 136 Configuring Secure Access Devices Guide...
Page 224: ...Copyright 2010 Juniper Networks Inc 206 Configuring Secure Access Devices Guide...
Page 234: ...Copyright 2010 Juniper Networks Inc 216 Configuring Secure Access Devices Guide...
Page 288: ...Copyright 2010 Juniper Networks Inc 270 Configuring Secure Access Devices Guide...
Page 300: ...Copyright 2010 Juniper Networks Inc 282 Configuring Secure Access Devices Guide...
Page 310: ...Copyright 2010 Juniper Networks Inc 292 Configuring Secure Access Devices Guide...
Page 312: ...Copyright 2010 Juniper Networks Inc 294 Configuring Secure Access Devices Guide...
Page 320: ...Copyright 2010 Juniper Networks Inc 302 Configuring Secure Access Devices Guide...
Page 322: ...Copyright 2010 Juniper Networks Inc 304 Configuring Secure Access Devices Guide...
Page 337: ...PART 6 Index Index on page 321 319 Copyright 2010 Juniper Networks Inc...
Page 338: ...Copyright 2010 Juniper Networks Inc 320 Configuring Secure Access Devices Guide...
Page 340: ...Copyright 2010 Juniper Networks Inc 322 Configuring Secure Access Devices Guide...