156
Kaspersky Administration Kit
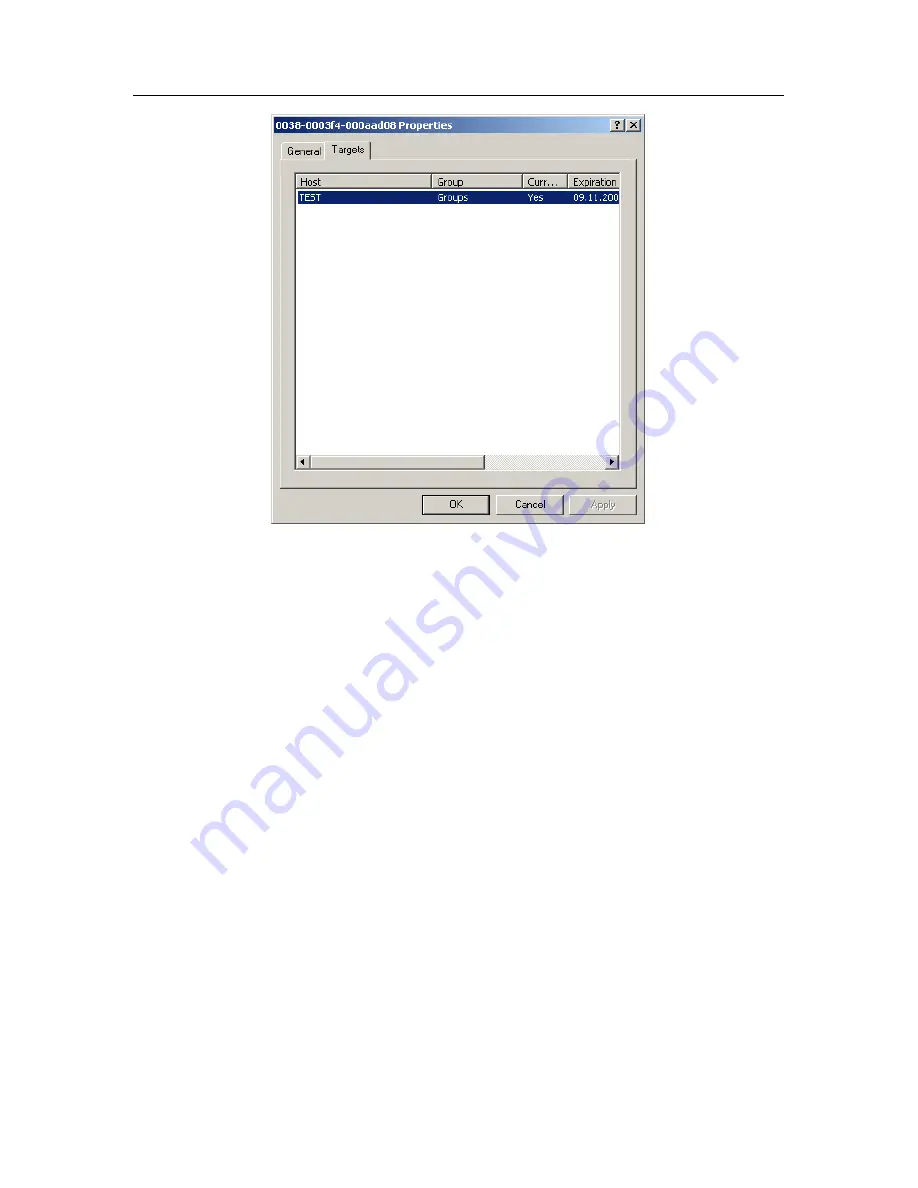
Figure 112. License key properties.
The
Targets
tab
You can check which license keys are installed for the application on a specific
client computer, by viewing the application properties configuration window.
5.1.3. Installing a license key
To install a license key,
create and launch a
license key installation
task.
The license key installation task can be created as a group, global or local
task (see section 3.2.1). When creating this task:
•
Specify the application for which you are installing this license
key as the application for which the task is being created;
•
specify
License key installation
as the task type.
During the task configuration state (see Figure 115), specify the license
key file
(*.key)
that must be installed.
If this key is intended to be used as the current key for the application and
to immediately replace the previous current key, check the
Use as the
current license key
box. If you are adding the key as a backup key, do
not check this box. The backup license key becomes the current license