-23-
z
z
z
z
z
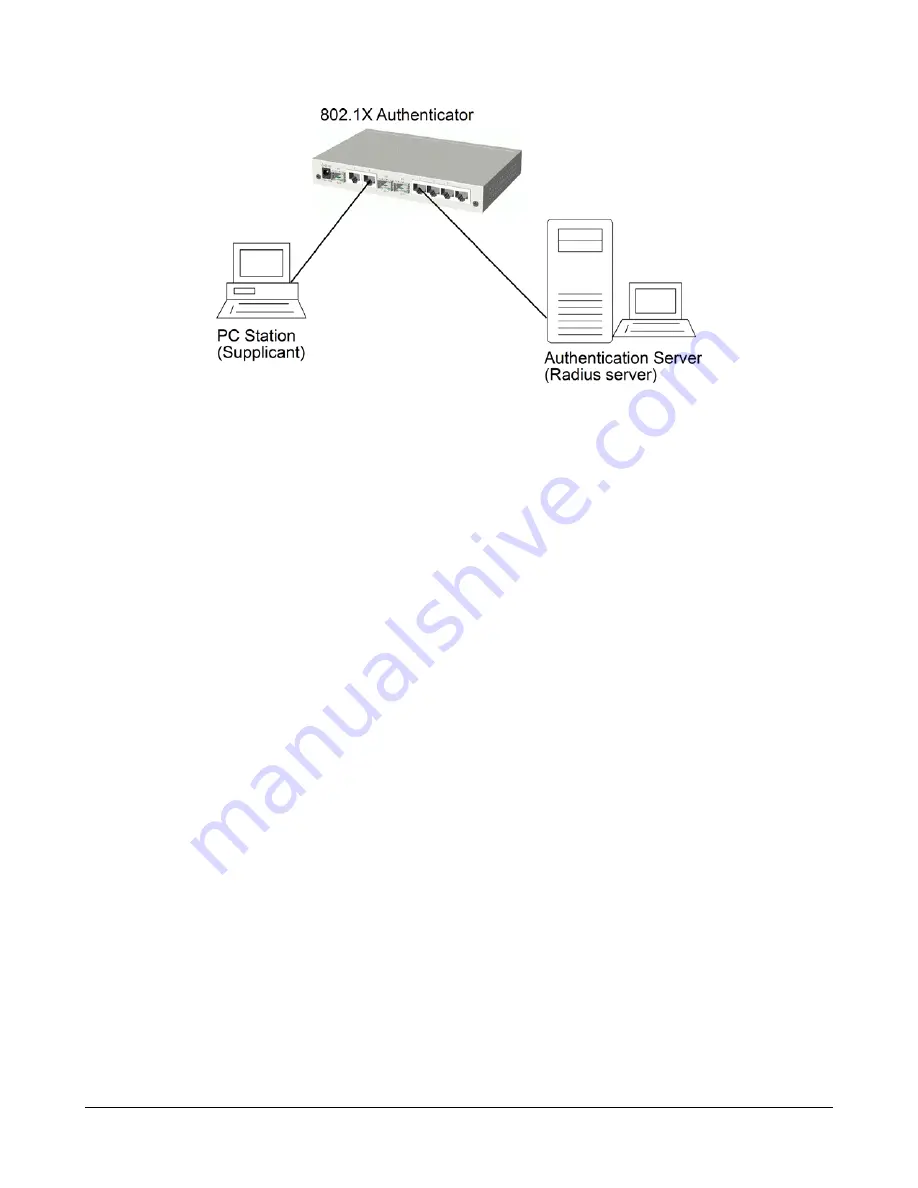
An 802.1X authenticator:
This is the port on the switch that has services to offer to an end device,
provided the device supplies the proper credentials.
z
z
z
z
z
An 802.1X supplicant:
This is the end device; for example, a PC that connects to a switch that is
requesting to use the services (port) of the device. The 802.1X supplicant must be able to respond to
communicate.
z
z
z
z
z
An 802.1X authentication server:
This is a RADIUS server that examines the credentials provided to
the authenticator from the supplicant and provides the authentication service. The authentication server is respon-
sible for letting the authenticator know if services should be granted.
The 802.1X authenticator operates as a go-between with the supplicant and the authentication server to
provide services to the network. When a switch is configured as an authenticator, the ports of the
switch must then be configured for authorization. In an authenticator-initiated port authorization, a client
is powered up or plugs into the port, and the authenticator port sends an Extensible Authentication
Protocol (EAP) PDU to the supplicant requesting the identification of the supplicant. At this point in the
process, the port on the switch is connected from a physical standpoint; however, the 802.1X process
has not authorized the port and no frames are passed from the port on the supplicant into the switching
engine. If the PC attached to the switch did not understand the EAP PDU that it was receiving from the
switch, it would not be able to send an ID and the port would remain unauthorized. In this state, the port
would never pass any user traffic and would be as good as disabled. If the client PC is running the
802.1X EAP, it would respond to the request with its configured ID. (This could be a username/
password combination or a certificate.)
After the switch, the authenticator receives the ID from the PC (the supplicant). The switch then
passes the ID information to an authentication server (RADIUS server) that can verify the identifica-
tion information. The RADIUS server responds to the switch with either a success or failure message.
If the response is a success, the port will be authorized and user traffic will be allowed to pass through
the port like any switch port connected to an access device. If the response is a failure, the port will
remain unauthorized and, therefore, unused. If there is no response from the server, the port will also
remain unauthorized and will not pass any traffic.
Summary of Contents for KGS-510F-B
Page 26: ... 26 4 4 System ...
















































