11g Wireless Security Router User Guide
- 23 -
from any others you have created.
Note:
The tunnel name set here does not always have to match
the name used at the other end of the tunnel. However, certain
VPN applications require a tunnel to have the same name at
both ends of the tunnel. If the other end point with which you
want to establish the tunnel dose not use this Wireless Security
Router, it is important that you give the other side precise set
up instructions and ensure that these are followed.
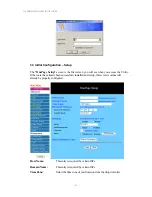
Local Secure Group:
There are some options that you can choose for this item
:
(1)
Subnet
Select this item to allow all the PCs on the LAN side access
to the tunnel.
Refer to the above figure as an example. All
Local Secure
Group
computers with IP Addresses 192.168.1.xxx will be
able to access the tunnel. When the Subnet setting is
selected, the default values of
0
should remain in the
IP
and
Mask
fields.
(2)
IP Address
8. Selecting this item allows only the specific
PC with the IP address you enter in the IP field to the tunnel.
Refer to the above figure as an example. Only the PC with IP
Address 192.168.1.101 will have the access from the local side
of tunnel.
(3)
IP Range
Selecting this item allows a specific group of PCs access to
the tunnel.
Refer to the above figure as an example. Only the PCs with
the IP addresses between 192.168.1.2 and 192.168.1.200
can access the local side of the tunnel.
Remote Secure Group:
(1)
Subnet
Select this item to allow all the PCs on the LAN side access
to the tunnel.
All
Remote Secure Group
computers with IP Addresses
192.168.2.xxx will be able to access the tunnel. When the
Subnet setting is selected, the default values of
0
should
remain in the
IP
and
Mask
fields.