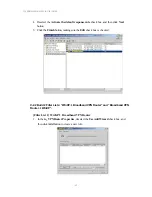
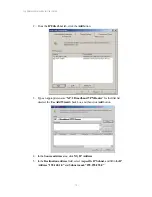
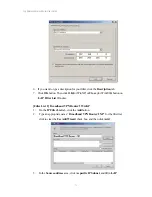
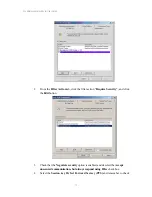
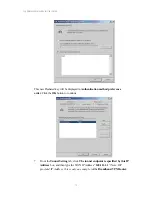
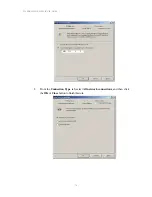
Reviews:
No comments
Related manuals for KWG-400

DWL-3500AP
Brand: D-Link Pages: 61

BDPP01
Brand: Baracoda Pages: 2

BDPP01
Brand: Baracoda Pages: 2

WA6020
Brand: H3C Pages: 27

Wifi bridge
Brand: jbmedia Pages: 6

PW5002
Brand: AMTC Pages: 81

241-0836
Brand: MasterForce Pages: 12

XV-5850
Brand: Z-Com Pages: 18

Infinity ZIP 500
Brand: Harman Pages: 7

BWAPG1000
Brand: Bountiful Pages: 1

TEW-812DRU
Brand: FCCID Pages: 90

W7 SERIES
Brand: Pakedge Device & Software Pages: 57

5411074162344
Brand: Constructor Pages: 34

9200
Brand: Kaba Pages: 2

NetGenie SOHO N300
Brand: Cyberoam Pages: 81

WL1100B-AR
Brand: AmbiCom Pages: 40

AP22
Brand: HPE Pages: 4

A76
Brand: Link Play Pages: 24