MPM-1000A Operator Manual
1000-7075 Rev E
15-1
15
APPENDIX A – NETWORK TRANSMISSION SECURITY
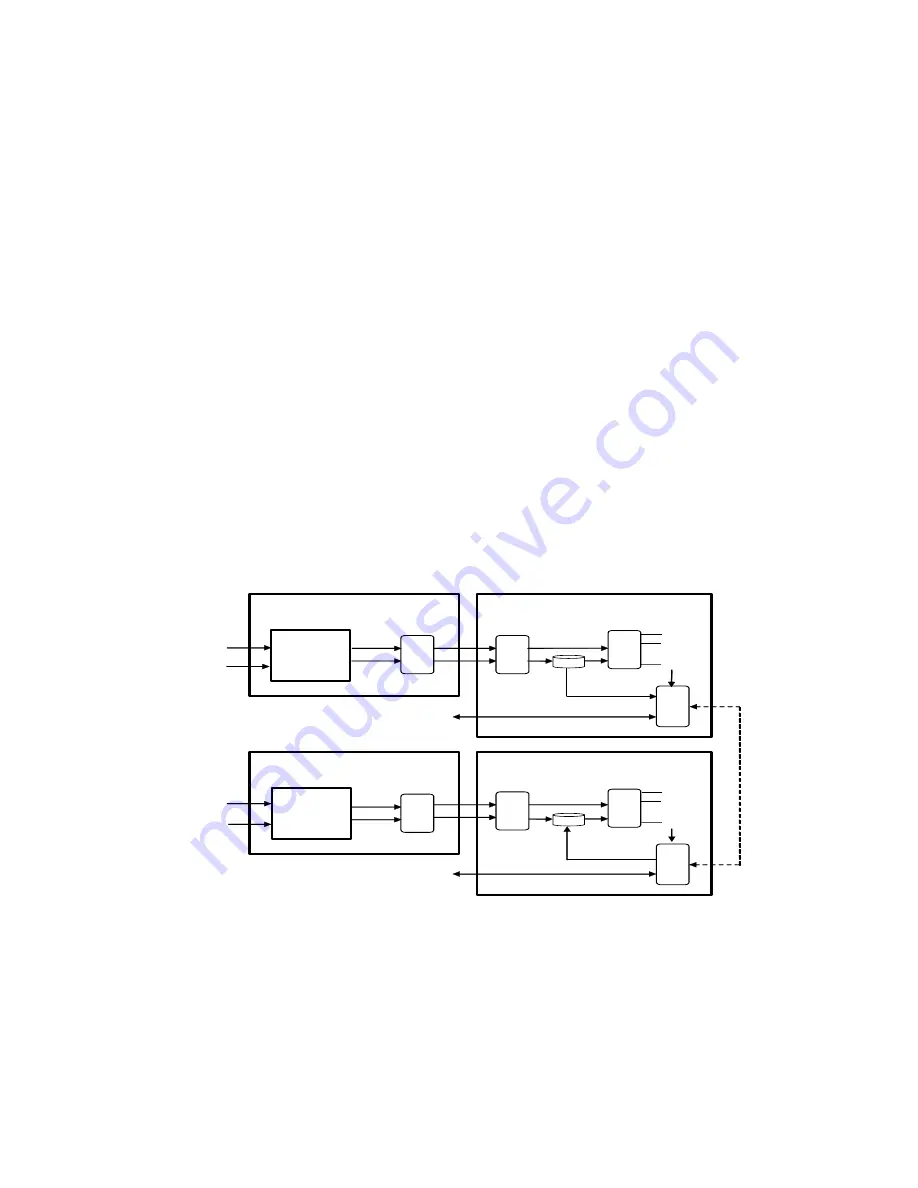
15.1 Keying Scheme
Figure 15-1 Overall Keying Scheme depicts the keying scheme used by the Modem in a
NCW network. A “split-knowledge” keying concept is employed, wherein two (2)
independent, externally supplied, keying parameters are required to produce the
operational message encryption key material (MEKs). The two (2) parameters are a
message seed key (MSK) and a passphrase. The seed key is retained by the Modem in
non-volatile storage and survives a power cycling of the Modem. The passphrase,
MEKs and all derived intermediate keying parameters are stored in volatile memory and
perish upon removal of Modem power.
Because both the MSK and TRANSEC
Passphrase are needed to derive operational keys, an idle (unpowered) Terminal will
not yield operational keys if compromised. Upon the reapplication of power, you must
enter the TRANSEC Passphrase in order to re-establish the operational TRANSEC
keys.
Figure 15-1 Overall Keying Scheme
S S H
A 2
N C T M P M -1 0 0 0
S S H
A 2
N T M P M -1 0 0 0 (s )
R F L in k
A 1
M E K
0
M E K
1
M E K
3 1
...
A 1
M E K
0
M E K
1
M E K
3 1
...
N C T C o n tr o lle r
S S H
M o d e m
C o n tr o l
S o ftw a re
S e e d K e y ( M S K )
P a s s p h r a s e
N T C o n tr o lle r
S S H
S e e d K e y
P a s s p h r a s e
(In itia l o n l y )
(M S K O T A R )
(M S K O T A R )
N e tw o rk D a ta T r a ffic
M o d e m
C o n tr o l
S o ftw a re
N e tw o rk D a ta T r a ffic
A1 = Key Derivation Function (1000-7124)
A2 = Traffic Encryption/Decryption (AES-256)
SSH = Secure Shell Protocol (encrypted/authenticated tunnel)
MEK = Message Encryption Key
NCT = Network Control Terminal
NT = Network Terminal













































