Lantronix
SM12XPA Web User Guide
33848 Rev. A
Page
321
of
473
Key-Chain Key ID
Each key in a keychain has a key string, authentication algorithm, sending lifetime, and receiving lifetime.
When the system time is within the lifetime of a key in a keychain, an application uses the key to authenticate
incoming and outgoing packets. The keys in the keychain take effect one by one according to the sequence of
the configured lifetimes. This way, the authentication algorithms and keys are dynamically changed to
implement dynamic authentication.
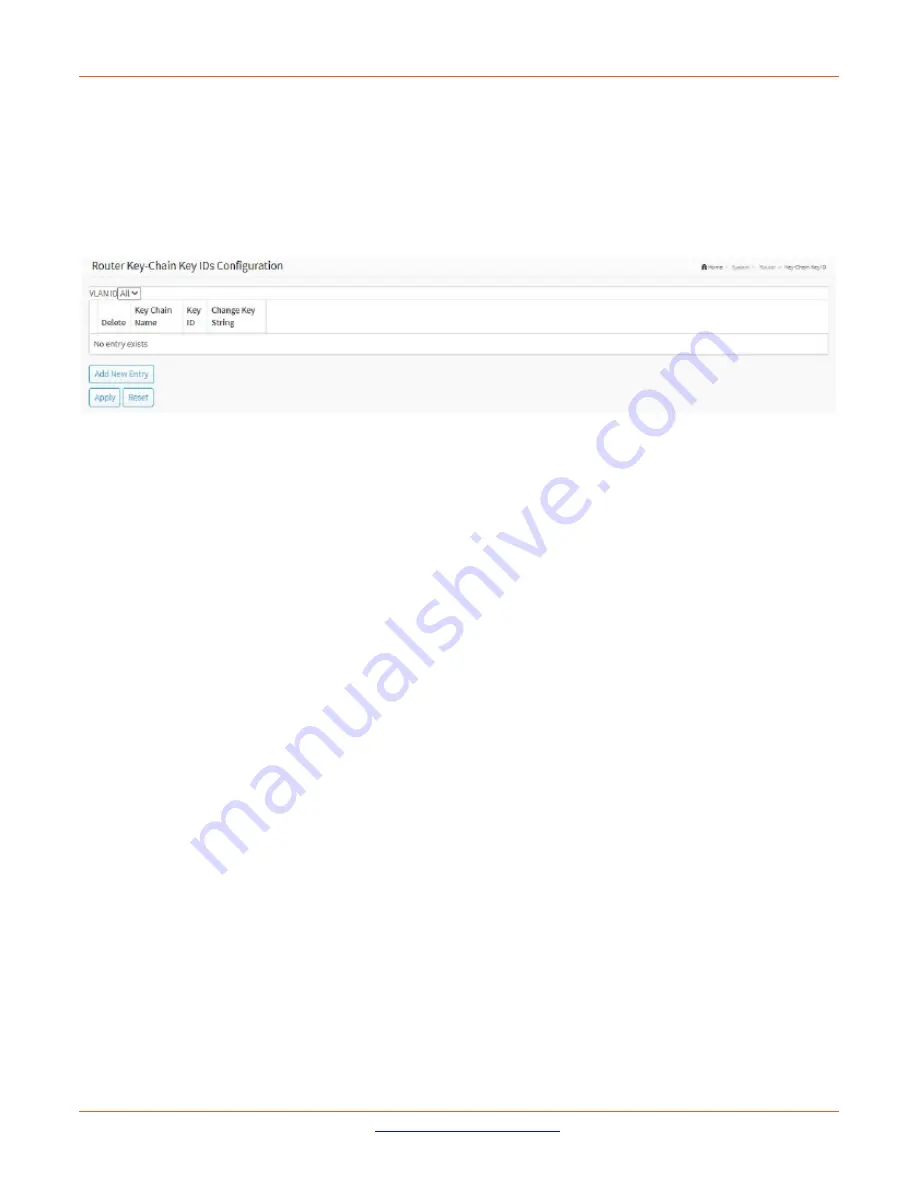
Figure 19-2: Router Key-Chain Key IDs Configuration
Parameter descriptions
:
VLAN
ID
: At the dropdown select the set of VIDs to display (All or a specific VLAN ID).
Delete
: Click to delete an existing entry.
Key Chain Name
: The given name of the key chain.
Key ID
: The assigned key chain identifier
Change Key String
:Click to change the current key chain.
Buttons
Add New Entry
: Click to add a new entry to the table.
Apply
: Click to save changes.
Reset
: Click to undo any changes made locally and revert to previously saved values.