Ju
ne
20
18
490 Legrand PDU User Guide
Device-Specific Settings
A bulk configuration file will NOT contain any device-specific information like the following list.
For further information, simply open the built-in bulk profile for a detailed list of 'excluded' settings.
Device name
SNMP system name, contact and location
Part of network settings (IP address, gateway, netmask and so on)
Device logs
Names, states and values of environmental sensors and actuators
TLS certificate
Server monitoring entries
Asset strip names and rack unit names
Outlet names and states
TLS Certificate Chain
A TLS server sends out a certificate to any client attempting to connect to it. The receiver determines
whether a TLS server can be trusted by verifying that server's certificate, using the certificate (chain) stored
on the receiver.
Therefore, to successfully connect to a TLS server, you must upload a valid certificate or (partial) certificate
chain to the receiver.
The uploaded certificate (chain) must contain all missing certificates "related to" that TLS server's certificate
in some way. Otherwise, the connection made to that TLS server will fail.
For information on how the uploaded certificate (chain) is related to a TLS server's certificate, see
What
is a Certificate Chain
(on page 490).
For an example of creating and uploading a TLS certificate to Legrand PDU, see
Illustration - GMAIL
SMTP Certificate Chain
(on page 492).
What is a Certificate Chain
If you are familiar with a certificate chain, you can ignore this topic and refer to
Illustration - GMAIL
SMTP Certificate Chain
(on page 492).
A certificate or a chain of certificates is used for trusting a TLS server that you want to connect.
The receiver, such as Legrand PDU, can trust a TLS server only after an appropriate certificate (chain) which
is "related to" that TLS server's certificate is uploaded to the receiver.
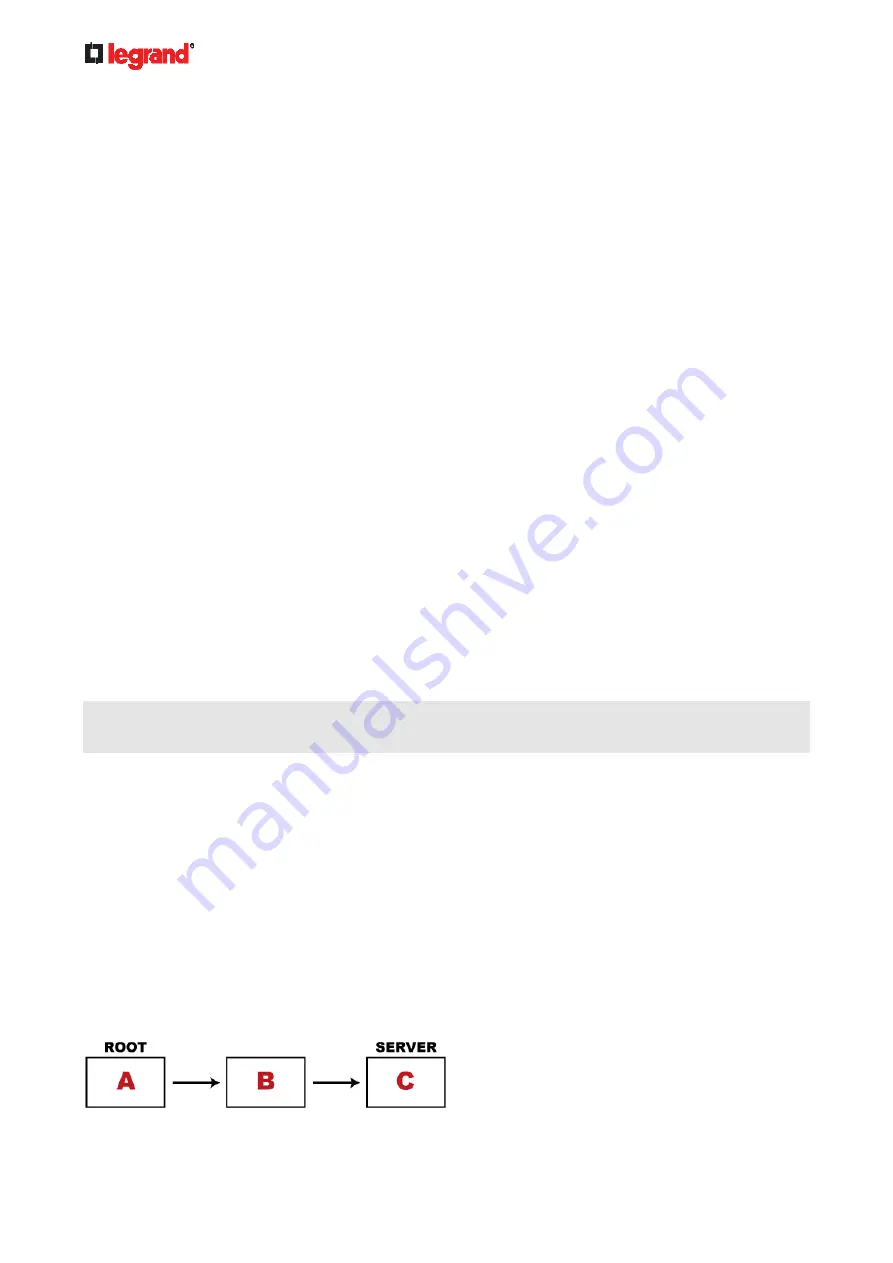
How a certificate chain is generated:
To explain how a TLS server's certificate is "related to" the certificate (chain) that is uploaded to the receiver,
we assume that there are three "related" certificates.
Certificate C
. The certificate issued to the TLS server you want to connect.
'Certificate C' is issued by the certificate authority (CA) entity called 'Issuer B'.
Certificate B
. The certificate issued to 'Issuer B'.
'Certificate B' is issued by a CA entity called 'Issuer A', and it is an intermediate certificate.
Certificate A
. The self-signed certificate issued by Issuer A. Issuer A is a root CA.
The above three certificates form a certificate path, which is called the "certificate chain".
















































