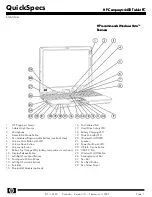
Hard disk security
To protect the computer from unauthorized security attacks, refer to the following tips to enhance security:
• Set a power-on password as well as a hard disk password. For security, a longer password is
recommended.
• The hard disk drive built into your computer can be protected by UEFI BIOS. To provide reliable security,
use the security chip and a security program with the Trusted Platform Module (TPM) management
feature. See “Setting the security chip” on page 51.
• If a Disk Encryption storage drive is installed in your computer, ensure to protect the contents of your
computer from unauthorized access by use of drive encryption software, such as Microsoft Windows
BitLocker
®
Drive Encryption.
• Before you dispose of, sell, or hand over your computer, delete the data stored on it. For more
information, see “Deleting data from your storage drive” on page 53.
Using Windows BitLocker Drive Encryption
To help protect your computer against unauthorized access, use the drive encryption software, such as
Windows BitLocker Drive Encryption.
Windows BitLocker Drive Encryption (referred to as BitLocker) is an integral security feature of some editions
of the Windows operating system. It can help you protect the operating system and data stored on your
computer, even if your computer is lost or stolen. BitLocker can encrypt all user and system files, including
the swap and hibernation files.
BitLocker uses the TPM to provide enhanced protection for your data and to ensure early boot component
integrity. A compatible TPM is defined as a V2.0 TPM.
To check the BitLocker status, go to Control Panel, view Control Panel by Category, and click
System and
Security
➙
BitLocker Drive Encryption
.
For more information, see the help system of the Windows operating system, or search for “Microsoft
Windows BitLocker Drive Encryption Step-by-Step Guide” on the Microsoft Web site.
Disk Encryption hard disk drive and Encryption solid-state drive
Some models contain the Disk Encryption hard disk drive, Encryption solid-state drive, or Encryption hybrid
drive. This encryption technology helps to protect your computer against security attacks on media, NAND
flash, or device controllers by use of a hardware encryption chip. For the efficient use of the encryption
feature, set a hard disk password for the internal storage drive.
Setting the security chip
Strict security requirements are imposed on network client computers that transfer confidential information
electronically. Depending on the options you ordered, your computer might have an embedded security chip
(a cryptographic microprocessor). With the security chip, you can do the following:
• Protect your data and system
• Strengthen access controls
• Secure communications
Before you start, print these instructions.
To set an item on the
Security Chip
submenu, do the following:
.
51
Summary of Contents for ThinkPad Yoga 11e Chromebook 3rd Gen
Page 1: ...L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 6: ...iv L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 56: ...38 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 60: ...42 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 66: ...48 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 88: ...70 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 124: ...106 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 126: ...108 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 132: ...114 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 138: ...120 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 139: ...Taiwan RoHS Appendix D Restriction of Hazardous Substances RoHS Directive 121 ...
Page 140: ...122 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 146: ...128 L380 L380 Yoga S2 3rd Gen and S2 Yoga 3rd Gen User Guide ...
Page 147: ......
Page 148: ......