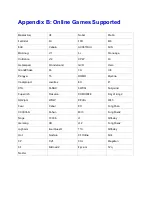
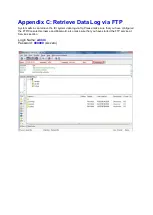
Summary of Contents for ICI-1000
Page 1: ...Internet Content Inspector ICI 1000 ICI 2000 User Manual v1 00...
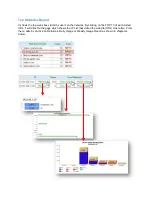
Page 20: ...Besides generating report by IP Administrator can also generate report by Account basis...
Page 38: ...4 Click on Play to play back the record MSN webcam session...
Page 58: ...Source Code When click on the following UI will pop up to display the source code of webpage...
Page 63: ...Sample HTTP Upload Download...
Page 65: ...Sample HTTP Video Stream...
Page 67: ...Sample HTTP Request Content...
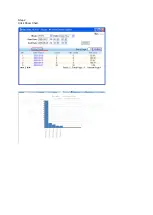
Page 159: ...Step 2 Click Show Chart...