93
Appendix D: Configuring IPSec between a Windows 2000 or XP Computer and the Router
How to Establish a Secure IPSec Tunnel
Wireless-G VPN Router with RangeBooster
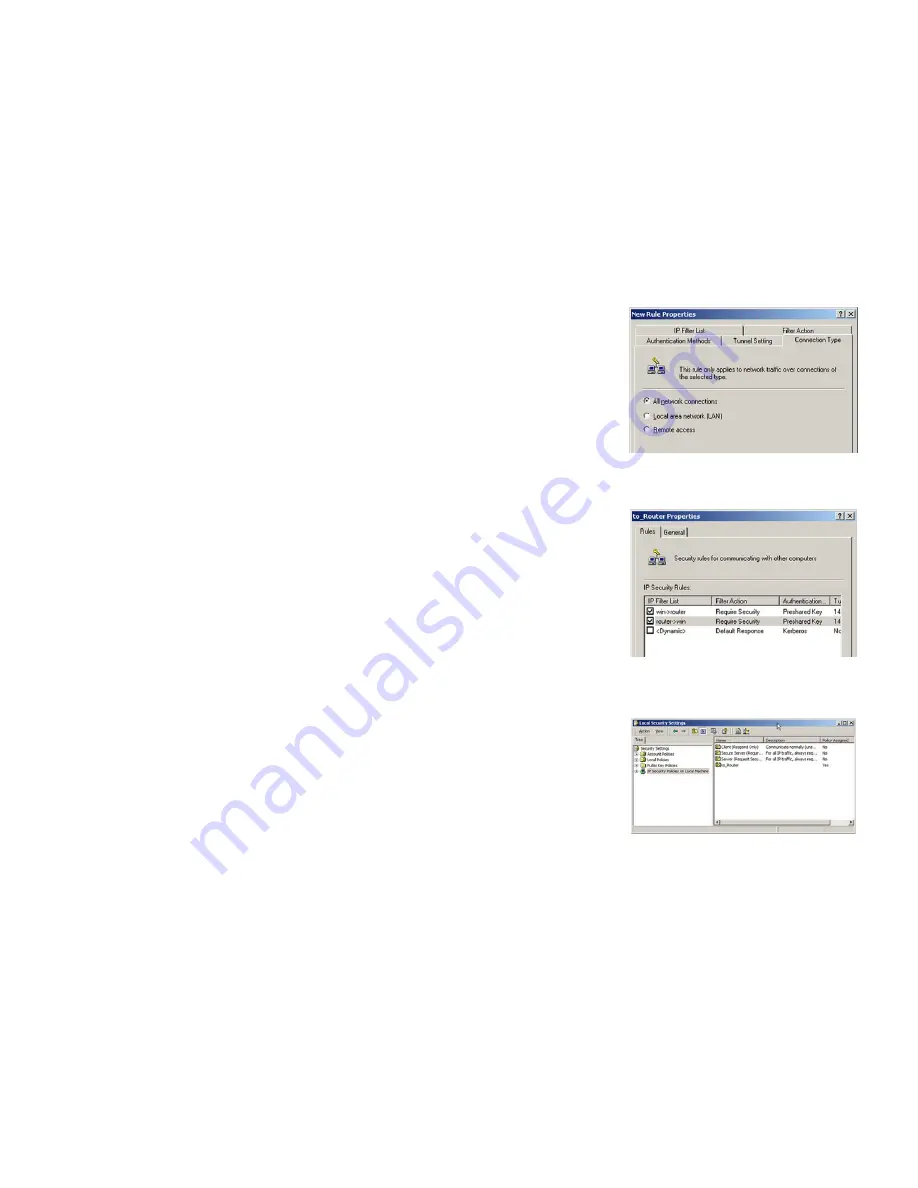
16. Click the
Connection Type
tab, and select
All network connections
. Then click the
OK
or
Close
button to
finish.
17. From the
Rules
tab, click the
OK
or
Close
button to return to the screen showing the security policies.
Step 4: Assign New IPSec Policy
In the
IP Security Policies on Local Machine
window, right-click the policy named
to_Router
, and click
Assign
. A
green arrow appears in the folder icon.
Figure D-25: Connection Type
Figure D-26: Rules
Figure D-27: Local Computer
Summary of Contents for WRV200
Page 1: ...Model No VPN Router with RangeBooster Wireless G WRV200 WIRELESS GHz 2 4802 11g User Guide ...
Page 10: ...Wireless G VPN Router with RangeBooster ...
Page 124: ...114 Appendix M Regulatory Information Wireless G VPN Router with RangeBooster ...
Page 125: ...115 Appendix M Regulatory Information Wireless G VPN Router with RangeBooster ...
Page 126: ...116 Appendix M Regulatory Information Wireless G VPN Router with RangeBooster ...
















































