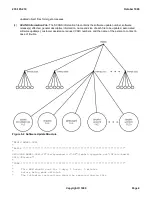
Assuming that the binary update files have been received and verified, the BX.25 data link is automatically
terminated.
5.3.4.3 Verification
A process is provided by the program update subsystem to verify software updates before overwriting the resident
software release. When the system receives the verification command, a check is made to confirm the existence
and correctness of all files and associated checksums.
If a software update error is detected through verification, the software update in question should be requested
again from SCANS. If the software update fails verification a second time, the Electronic Switching Assistance
Center (ESAC) and the RTAC should be notified.
5.3.4.4 Activation
NOTE:
This section is a general description of a software update activation. Later software releases allowed for
enhanced program update capabilities through the use of a menu-driven craft interface.
After the software updates have been successfully verified, an executable message file for a specific software
update is created. The message file contains an instruction set for activating a particular software update. The
UPD:BWMNO;
message contains a software update number that corresponds to a specific message file and the
pathname of the message file. Only one executable message file can be executed in the system at any one time.
The previous executable message file is overwritten each time the
UPD:BWMNO;
message is input.
NOTE:
The software updates must be activated in sequential order. The executable message file contains four
user accessible sections. Only three sections are used for normal installation. The fourth section is used for
emergency backout. Once an executable message file has been created for a specific software update,
that software update can be installed by entering forms of the
UPD:EXEC;
message as follows:
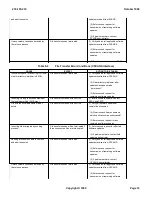
(1)
Apply
: The APPLY section is used to place an update into a temporary mode. It is executed by
entering the
UPD:EXEC:CMD,APPLY;
message.
(2)
Soak
: The SOAK section contains the recommended soak interval for a software update. A soak
interval is a period of time when the software update is tested and observed for proper operation.
Although it is possible to execute the SOAK section by using the
UPD:EXEC:CMD:SOAK;
message, each step of the SOAK section, where applicable, should be performed on a manual
basis to allow close observation of the soak interval.
(3)
Official
: The OFFICIAL section is used to make the temporary update permanent following
successful completion of the soak interval. It is executed by entering the
UPD:EXEC:CMD:OFFICIAL;
message.
(4)
Backout
: The BACKOUT section is used only when it becomes necessary to back out of a
temporary software update. It is executed by entering the
UPD:EXEC:CMD:BKOUT;
message.
The APPLY, OFFICIAL, and BACKOUT sections each contain one or more executable messages. The SOAK
section may or may not contain messages. A copy of the current executable message file may be obtained by using
the
UPD:BWMNO:LIST,ALL;
message.
The normal progression for software update activation is to execute the APPLY section first, followed by the SOAK
section, and finally the OFFICIAL section.
If the system is rebooted when temporary updates are in place (other than switching module updates), the
235-105-210
October 1999
Copyright © 1999
Page 7
Summary of Contents for 5ESS-2000
Page 96: ...235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 184: ...235 105 210 October 1999 Copyright 1999 Page 3 ...
Page 300: ...13 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 55 ...
Page 339: ...7 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 13 ...
Page 342: ...235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 359: ...235 105 210 October 1999 Copyright 1999 Page 5 ...
Page 609: ...2 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 12 ...
Page 676: ...235 105 210 October 1999 Copyright 1999 Page 9 ...
Page 792: ...3 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 9 ...
Page 799: ...Figure 11 36 3 1 Cleaning Points 235 105 210 October 1999 Copyright 1999 Page 7 ...
Page 801: ...235 105 210 October 1999 Copyright 1999 Page 9 ...
Page 839: ...2 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 16 ...
Page 999: ...2 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 13 ...
Page 1008: ...Figure 11 55 1 CTSNS DIP Switch Settings 235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 1011: ...235 105 210 October 1999 Copyright 1999 Page 5 ...
Page 1053: ...235 105 210 October 1999 Copyright 1999 Page 15 ...
Page 1289: ...Figure 15 17 2 AMATPS Data Link 235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 1292: ...235 105 210 October 1999 Copyright 1999 Page 5 ...
Page 1303: ...9 STOP YOU HAVE COMPLETED THIS PROCEDURE 235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 1360: ...Figure 15 47 2 Typical SCANS III Link Diagram 235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 1372: ...235 105 210 October 1999 Copyright 1999 Page 2 ...
Page 1374: ...235 105 210 October 1999 Copyright 1999 Page 4 ...
Page 1421: ...Table 1 1 O M Checklist 235 105 210 October 1999 Copyright 1999 Page 3 ...