B
EST
U
SAGE
P
RACTICES
T
HREAT
A
NALYSIS
R
EPORTER
U
SAGE
S
CENARIOS
M86 S
ECURITY
I
NSTALLATION
G
UIDE
67
Step C: Investigate the user’s Internet activity in other gauges
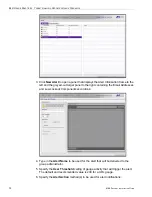
1. To find out which other gauges the same user is currently affecting, return to the
Gauge Ranking table by going to the lower left corner of the Threat View User
panel and clicking the
Back
button. In the User Name column, click that user’s
link to display the User Summary panel for that user:
Note the Gauge Readings frame to the right with the Total score for each Gauge
Name listed.
2. Select a Gauge Name to investigate, which activates the Threat View button
below:
3. Click
Threat View
to display the Threat View User panel (see Step A2).
Summary of Contents for HL
Page 95: ......