MC8687P Mini PCIe WLAN Client Card User’s Guide
________________________________________________________________________
________________________________________________________________________
Doc. No________ Rev.V1.0
Confidential
Copyright © 2007 Marvell
Page
26
Document Classification: Proprietary Information
December 28, 2007
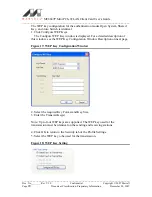
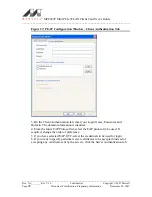
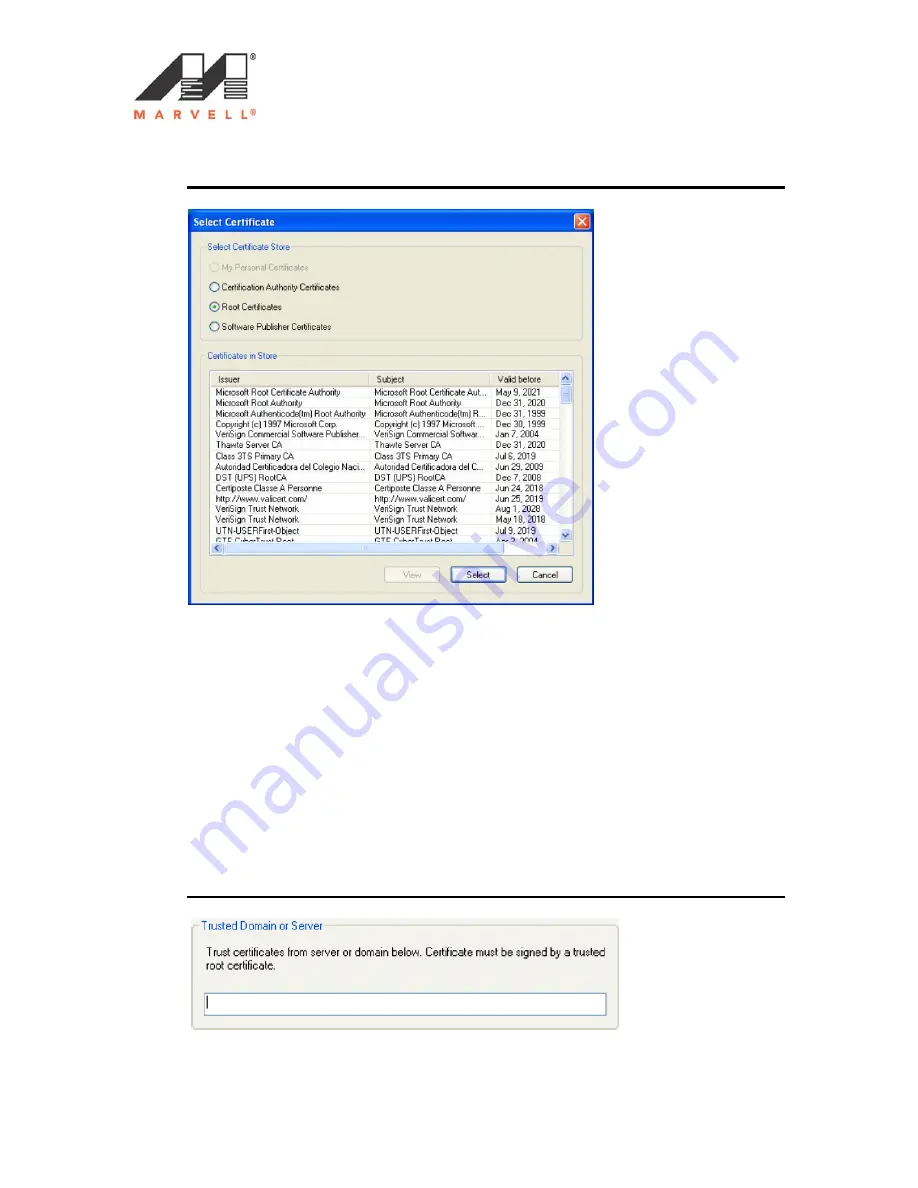
Figure 24: Select Certificate Window (Server Certificates)
10. On the Select Certificate window, select the Certificate Store.
11. From the Certificate in Store list, click the certificate to be the server
authentication.
Note: If the required certificate is not you installed on your system or if you do
not know which certificate to use, contact your network administrator.
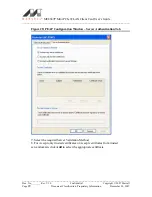
12. Click
Select
to confirm your selection and to return to the EAP/TLS (Use
Certificated) window.
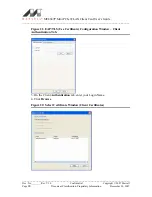
13. If you have selected Accept certificates from trusted server/domain, enter the
appropriate server name or domain name into the Trusted Domain or Server box.
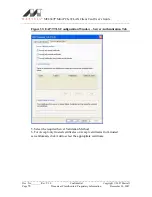
Figure 25: Server Authentication – Trusted Domain or Server
14. Click
OK
to return to the Security tab of the Profile Settings.