© Microhard Systems Inc.
65
4.0 Configuration
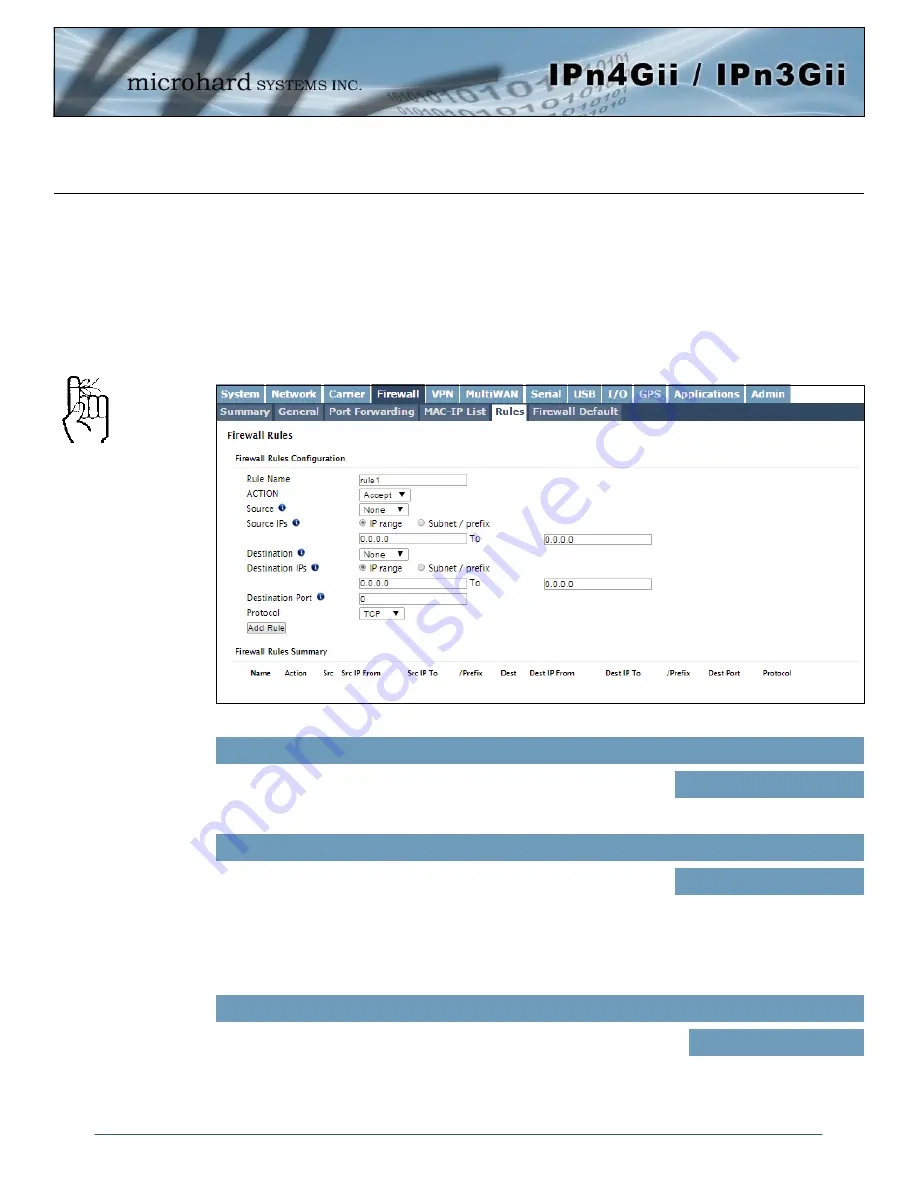
Image 4-4-6: Firewall > Rules
4.4.5 Firewall > Rules
Once the firewall is turned on, rules configuration can be used to define specific rules on how local and
remote devices access different ports and services. MAC List and IP List are used for general access, and
are applied before rules are processed.
It is highly recommended to block as much traffic as possible from the modem, especially when using a
public IP address. The best security would to be to allow traffic only from trusted IP addresses, and only
the specific ports being used, and block everything else. Not configuring the firewall and the firewall rules
correctly could result in unpredictable data charges from the cellular carrier.
Rule Name
The rule name is used to identify the created rule. Each rule must have a
unique name and up to 10 characters can be used.
Values (10 Chars)
characters
Action
The Action is used to define how the rule handles the connection request.
ACCEPT will allow a connection, while REJECT (error) and DROP
(quietly dropped), will refuse connections.
This is configured based on how the
WAN/Carrier Request
and
LAN to
WAN/Carrier Access Control
are configured in the previous menus.
Values (selection)
ACCEPT
DROP
REJECT
Source
Select the zone which is to be the source of the data traffic. 3G/Cellular
applies to the connection to the cellular carrier. The LAN/LAN1/USB refers
to local connections on the IPnXGii.
Values
LAN/LAN1/WAN/Cell/USB/
None
Refer to Appendix D for an
example of how to set up a
firewall to block all
connections and then add
access to only specific IP’s
and Ports.
Appendix D: Firewall
Example
















































