Configuring Access Point Security
Security measures for the access point and its WLANs are critical. Use the available access point
security options to protect the access point LAN from wireless vulnerabilities, and safeguard the
transmission of RF packets between the access point and its associated MUs.
WLAN security can be configured on an ESS by ESS basis on the access point. Sixteen separate
ESSIDs (WLANs) can be supported on an access point, and must be managed (if necessary) between
the 802.11a and 802.11b/g radio. The user has the capability of configuring separate security policies
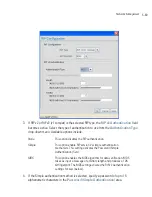
for each WLAN. Each security policy can be configured based on the authentication (Kerberos, 802.1x
EAP) or encryption (WEP, KeyGuard, WPA/TKIP or WPA2/CCMP) scheme best suited to the coverage
area that security policy supports.
The access point can also create VPN tunnels to securely route traffic through a IPSEC tunnel and
block transmissions with devices interpreted as Rogue APs.
Summary of Contents for AP 5131 - Wireless Access Point
Page 1: ...AP 51xx Access Point Product Reference Guide ...
Page 3: ...AP 51xx Access Point Product Reference Guide 72E 103901 01 January 2008 ...
Page 4: ......
Page 44: ...AP 51xx Access Point Product Reference Guide 1 28 ...
Page 76: ...AP 51xx Access Point Product Reference Guide 2 32 ...
Page 92: ...AP 51xx Access Point Product Reference Guide 3 16 ...
Page 588: ...AP 51xx Access Point Product Reference Guide 8 254 ...
Page 610: ...AP 51xx Access Point Product Reference Guide 9 22 3 Define a mesh supported WLAN ...
Page 623: ...Configuring Mesh Networking 9 35 3 Determine the Radio MAC Address and BSSID MAC Addresses ...
Page 653: ...Adaptive AP 10 25 line con 0 line vty 0 24 end ...
Page 654: ...AP 51xx Access Point Product Reference Guide 10 26 ...
Page 666: ...AP 51xx Access Point Product Reference Guide A 12 ...
Page 690: ...AP 51xx Access Point Product Reference Guide C 4 ...
Page 696: ...AP 51xx Access Point Product Reference Guide IN 10 ...
Page 697: ......