8-77
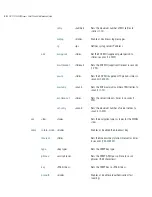
AP7131N>admin(network.wireless.wlan.hotspot.radius)> show
Description:
Shows Radius hotspot server details.
Syntax:
Example:
admin(network.wireless.wlan.hotspot.radius)>
show radius 1
Warning: This will display secure information,
Do you want to continue? (n/y?)y
WLAN 1
Hotspot Mode
: enable
Primary Server Ip adr
: 157.235.12.12
Primary Server Port
: 1812
Primary Server Secret
: ******
Secondary Server Ip adr
: 0.0.0.0
Secondary Server Port
: 1812
Accounting Mode
: enable
Accounting Server Ip adr
: 157.235.15.16
Accounting Server Port
: 1813
Accounting Server Secret
: ******
Accounting Timeout
: 10
Accounting Retry-count
: 3
Session Timeout Mode
: enable
admin(network.wireless.wlan.hotspot.radius)>
For information on configuring the Hotspot options available to the access point using the applet (GUI), see
Configuring WLAN
Hotspot Support on page 5-48
.
show
radius
<idx>
Displays Radius hotspot server details per index (1-16)
Summary of Contents for AP-7131N-FGR
Page 1: ...AP 7131N FGR Access Point Product Reference Guide ...
Page 3: ...AP 7131N FGR Access Point Product Reference Guide 72E 126727 01 Revision A September 2009 ...
Page 4: ......
Page 55: ...Hardware Installation 2 11 ...
Page 68: ...AP 7131N FGR Access Point Product Reference Guide 2 24 ...
Page 90: ...AP 7131N FGR Access Point Product Reference Guide 3 22 ...
Page 148: ...AP 7131N FGR Access Point Product Reference Guide 4 58 ...
Page 300: ...AP 7131N FGR Access Point Product Reference Guide 6 72 ...
Page 338: ...AP 7131N FGR Access Point Product Reference Guide 7 38 ...
Page 635: ...Configuring Mesh Networking 9 23 5 Define a channel of operation for the 802 11a n radio ...
Page 648: ...AP 7131N FGR Access Point Product Reference Guide 9 36 ...
Page 672: ...AP 7131N FGR Access Point Product Reference Guide 10 24 line con 0 line vty 0 24 end ...
Page 692: ...AP 7131N FGR Access Point Product Reference Guide B 14 ...
Page 698: ...AP 7131N FGR Access Point Product Reference Guide B 20 ...
Page 702: ...AP 7131N FGR Access Point Product Reference Guide C 4 ...
Page 707: ......