Motorola Cellular Gateway NC800 User Guide Version 2.0
Page 9 of 110
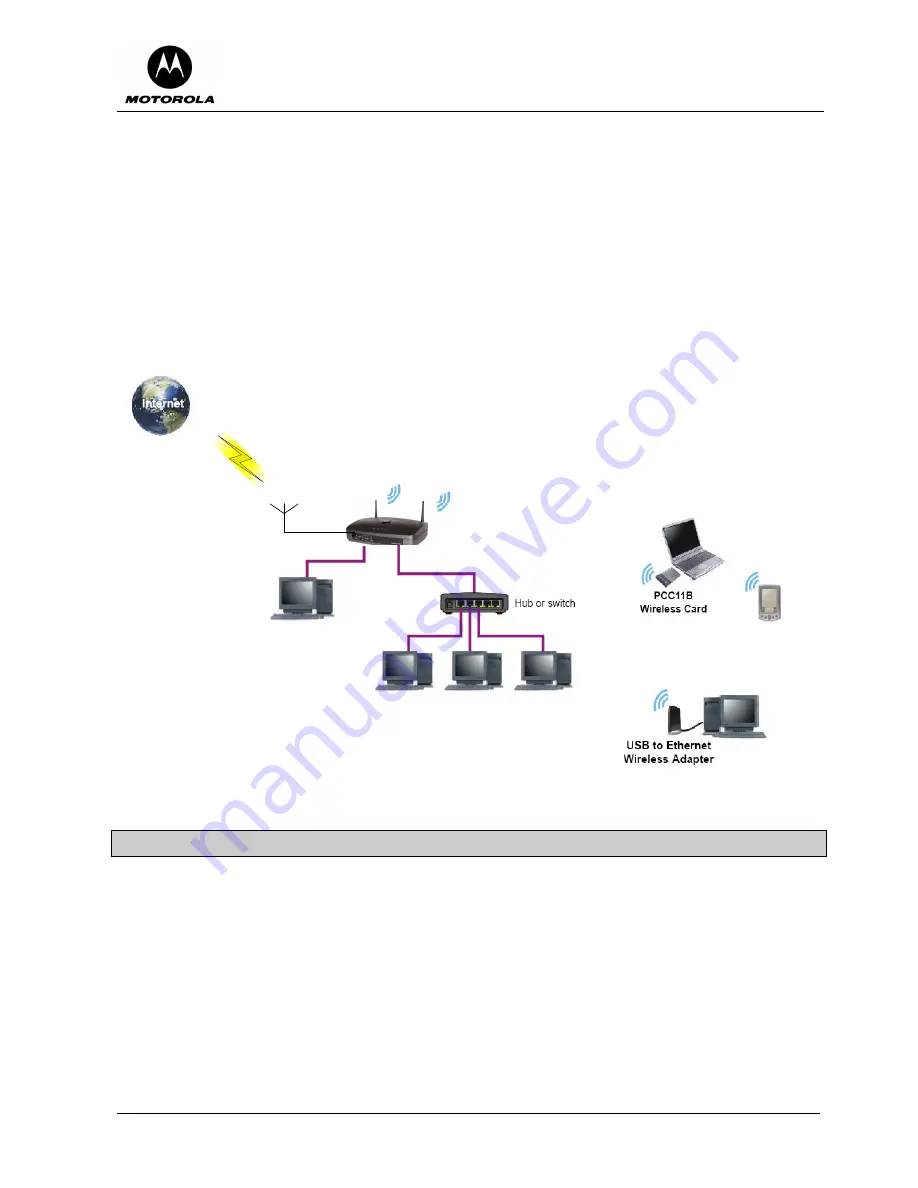
The sample application shown in Figure 2 is slightly more complex and is more typical of a small office
environment. It contains the following devices, all protected by the Motorola Cellular Gateway NC800 firewall:
•
A PDA connected through the wireless IEEE 802.11b connection.
•
One desktop PC on a wireless connection. A Motorola USB 802.11b Wireless Adapter (an optional PC
accessory available from Motorola) or any other 802.11b/g wireless adapter can be used to connect
your PC USB port to the Motorola Cellular Gateway NC800 via a wireless connection.
•
A laptop PC on a wireless connection. The wireless connection can be made using a Motorola PCC11b
Wireless Card or any other 802.11b/g wireless card in the PCMCIA slot of the laptop (the PCC11b
Wireless Card is an optional laptop accessory available from Motorola).
•
Three computers connected to the LAN 1 Ethernet port via a hub or switch.
•
A fourth computer connected to the LAN 2 Ethernet port. This could be a De-Militarized Zone (DMZ)
computer.
Motorola Cellular Gateway
CDMA Antenna
PDA
Wireless LAN
devices
LAN2
LAN1
Figure 2. Typical application of a Motorola Cellular Gateway NC800 in a small office environment.
Security
The Motorola Cellular Gateway NC800 provides the following security mechanisms:
•
A firewall to protect the Motorola Cellular Gateway NC800 LAN from undesired attacks over the Internet
•
The capability to set up a DMZ
•
Security measures to prevent eavesdropping of wireless data (including WEP / WPA-PSK encryption
and authentication)
•
Multiple tunnel Virtual Private Network (VPN) pass-through operation
•
Access control to configure the Motorola Cellular Gateway NC800.
The subsections below provide some introductory information regarding the security technology listed above.
More details are provided in the relevant subsections of the Detailed Motorola Cellular Gateway NC800
Configuration section as well as in the relevant Glossary entries.
A full discussion of network security is beyond
the scope of this document.










































