5 - 132 WiNG 5.6 Access Point System Reference Guide
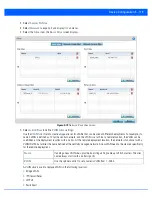
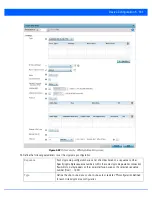
14. Select
OK
to save the changes made within the
Peer Configuration
screen. Select
Reset
to revert to the last saved
configuration.
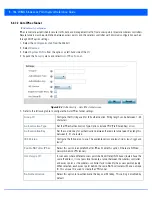
15. Select the
Transform Set
tab.
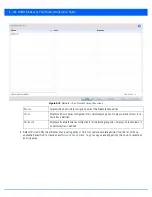
Create or modify
Transform Set
configurations to specify how traffic is protected within crypto ACL defining the traffic
that needs to be protected.
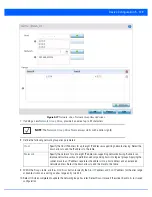
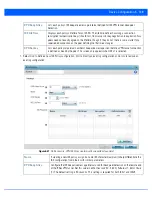
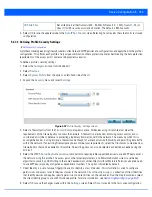
IP Type
Enter either the IP address or FQDN hostname of the IPSec VPN peer used in the tunnel
setup. If
IKEv1
is used, this value is titled
IP Type
, if
IKEv2
is used, this parameter is titled
Select IP/Hostname
.
Authentication Type or
Local Authentication
Type
Select either
pre-shared key
(PSK) or RSA.
Rivest, Shamir, and Adleman
(RSA) is an
algorithm for public key cryptography. It’s the first algorithm known to be suitable for
signing, as well as encryption If using
IKEv2
, this screen displays both
local
and
remote
authentication
options, as both ends of the VPN connection require authentication.
RSA
is the default value for both local and remote authentication (regardless of IKEv1 or
IKEv2).
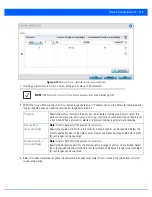
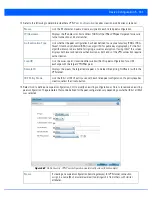
Authentication Value
or
Local Authentication
Value
Define the authentication string (shared secret) that must be shared by both ends of the
VPN tunnel connection. The string must be from 8 - 21 characters long. If using
IKEv2
,
both a local and remote string must be specified for handshake validation and both ends
(local and remote) of the VPN connection.
Local Identity
Select the access point’s local identifier used with this peer configuration for an IKE
exchange with the target VPN IPSec peer. Options include
IP Address
,
Distinguished
Name
,
FQDN
,
and
string
. The default setting is string.
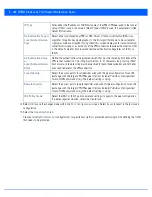
Remote Identity
Select the access point’s remote identifier used with this peer configuration for an IKE
exchange with the target VPN IPSec peer. Options include
IP Address
,
Distinguished
Name
,
FQDN
,
and
string
. The default setting is string.
IKE Policy Name
Select the IKEv1 or IKE v2 policy name (and settings) to apply to this peer configuration.
If a policy requires creation, select the
Create
icon.
Summary of Contents for WiNG 5.6
Page 1: ...Motorola Solutions WiNG 5 6 ACCESS POINT SYSTEM REFERENCE GUIDE ...
Page 2: ......
Page 22: ...8 WiNG 5 6 Access Point System Reference Guide ...
Page 26: ...1 4 WiNG 5 6 Access Point System Reference Guide ...
Page 38: ...2 12 WiNG 5 6 Access Point System Reference Guide ...
Page 74: ...3 36 WiNG 5 6 Access Point System Reference Guide ...
Page 468: ...6 2 WiNG 5 6 Access Point System Reference Guide Figure 6 1 Configuration Wireless menu ...
Page 568: ...6 102 WiNG 5 6 Access Point System Reference Guide ...
Page 614: ...7 46 WiNG 5 6 Access Point System Reference Guide ...
Page 660: ...8 46 WiNG 5 6 Access Point System Reference Guide ...
Page 716: ...9 56 WiNG 5 6 Access Point System Reference Guide ...
Page 730: ...10 14 WiNG 5 6 Access Point System Reference Guide ...
Page 982: ...14 20 WiNG 5 6 Access Point System Reference Guide ...
Page 984: ...A 2 WiNG 5 6 Access Point System Reference Guide ...
Page 1046: ...B 62 WiNG 5 6 Access Point System Reference Guide ...
Page 1047: ......